Fully recovering from the SolarWinds hack will take the US government from a year to as long as 18 months, according to the head of the agency that is leading Washington’s recovery.
Gootloader appears to have expanded its payloads further as it now uses SEO poisoning to deliver an array of malware payloads against users in South Korea, Germany, France, and the U.S.
A Blackberry report unveiled that state-backed actors often collaborate with mercenary APT groups to excel in attacks. Simultaneously, it helps state-backed actors lie low with their game plan.
After studying millions of email-based attacks, researchers note a unique trend in malware-stealing attempts and disclose details about the success recipe of a top malware used by them.
Singapore has released guidelines on heightened risks businesses in the financial services industry (FSI) now face as remote work practices take hold and how they can mitigate such risks.
Dragos uncovers a total of 15 threat groups targeting industrial organizations, with four new groups joining in 2020. The new groups are efficient enough to sabotage control systems.
A threat actor stole the personally identifiable information of recipients of the US Congressional Medal of Honor and used their personal data to purchase goods from American military exchanges.
Steganography is used to hide code, images, and video content within other content of file formats, and in this case, the researchers have found BMP files that contain malicious ObliqueRAT payloads.
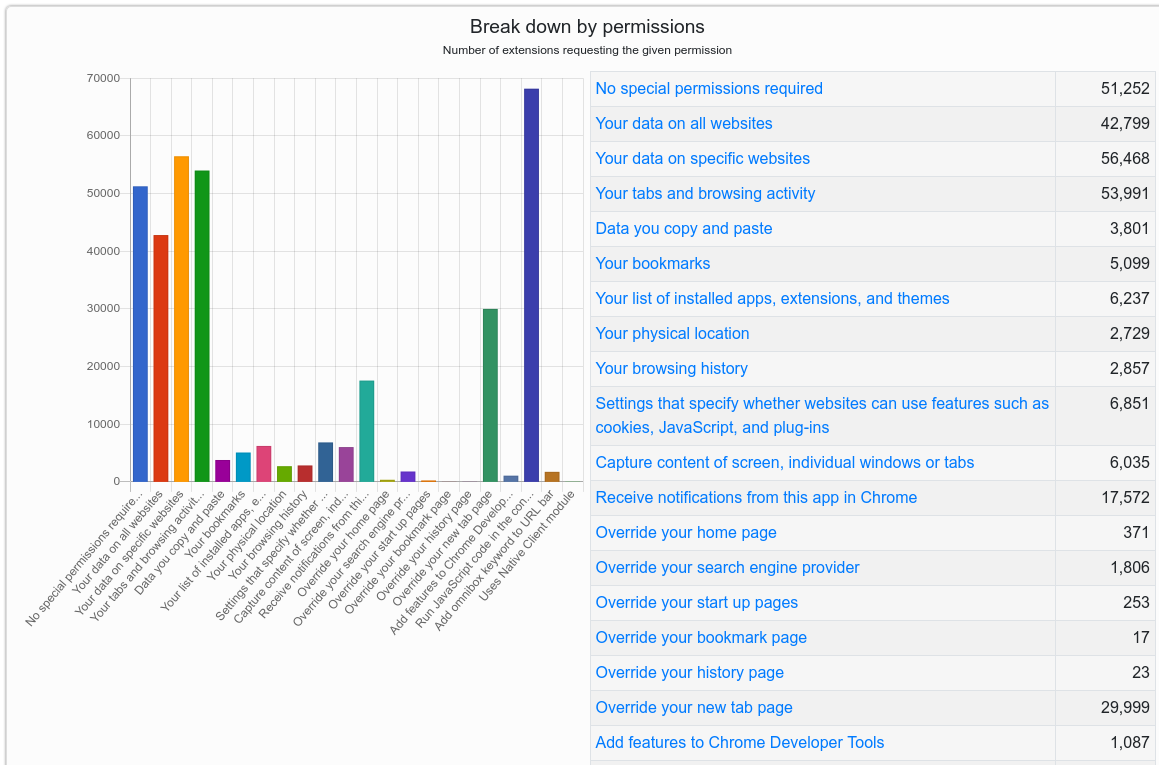
Infatica uses the browser of anyone who has an extension injected with its code to route web traffic for the company’s customers, including marketers or anyone able to afford its subscription charges.
Google this week announced the release of patches for 37 vulnerabilities as part of the Android security updates for March 2021, including a fix for a critical flaw in the System component.