Recent supply chain attacks prompted cybersecurity professionals, under the auspices of Cybersecurity Collaborative, to stand up a task force focused on minimizing third-party risk.
Loading remotely hosted images instead of embedding them directly into emails is one of the latest tricks employed by phishers to bypass email filters that cannot detect such images in real-time.
All extensions were developed by a software company named “Oink and Stuff,” specialized in creating Android apps and browser extensions for Chrome, Firefox, Opera, and Microsoft Edge.
Over the past week, security researcher MalwareHunterTeam has seen an uptick in verified Twitter accounts hacked in a scam promoting another fake Elon Musk cryptocurrency giveaway.
In the wake of several recent attacks, the adoption of ransomware tactics points to the fact that these APT groups are aiming for financial gains as these attacks don’t count as espionage targets.
A security flaw in Ring’s Neighbors app, which lets users anonymously alert nearby residents to crime and public-safety issues, was exposing precise locations and home addresses of those who posted.
With broad vulnerabilities across all levels of government and firms, the US must reevaluate its approach to advancing its interests while also protecting itself in this emerging fifth domain of war.
According to a new report from VC firm DataTribe, the trend reflects the way the cybersecurity industry is resetting after a wave of venture capital began dropping off about two years ago.
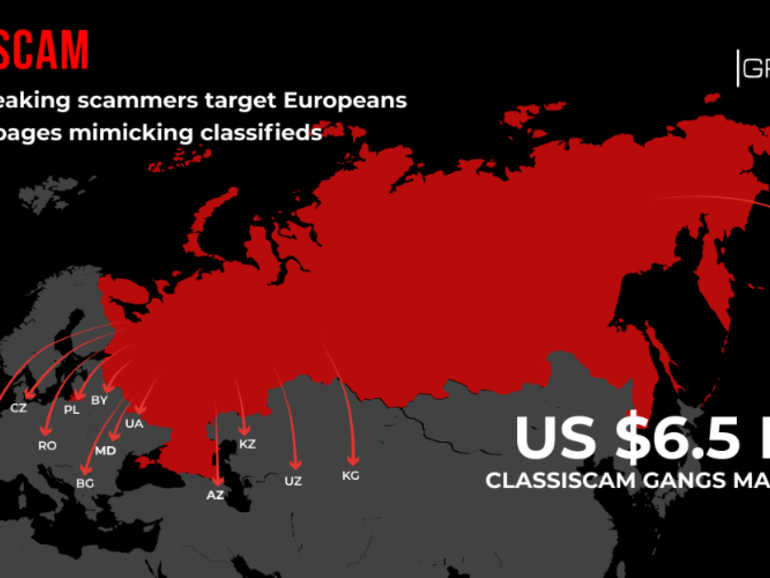
A newly uncovered Russian-based cybercrime operation has helped classified ads scammers steal more than $6.5 million from buyers across the US, Europe, and former Soviet states.
Brad Smith, president of Microsoft, warned of the increasing cyber-threats to society as technology plays a more powerful role in our lives during his keynote address at the Consumer Electronics Show (CES) 2021.