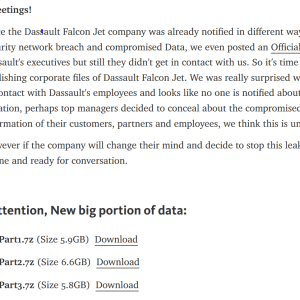
The incident also exposed information belonging to employees’ spouses and dependents, states the notice of data breach sent by the US subsidiary of French aerospace company Dassault Aviation.
WhatsApp is making several private groups available across the Web by indexing group chat invites, as their links can be accessed by anyone using a simple search on Google.
The data breach stemmed from exposed Git directories and credentials, which allowed the researchers to clone Git repositories and gather a large amount of personally identifiable information (PII).
The boom in online shopping has made the retail sector vulnerable to cyberattacks. A trend has been observed in how attackers are targeting users and pilfering card data.
Researchers reported a supply chain attack campaign by a North Korean APT group aimed at the users of a private stock investment service.
With the investigation ongoing, Judiciary said federal courts across the country will be adding new security procedures aimed at protecting highly sensitive confidential documents filed with courts.
The new Bureau of Cyberspace Security and Emerging Technologies (CSET) will help lead diplomatic efforts around these topics, including working to prevent cyber conflicts with adversarial nations.
First identified in 2014, Emotet has been regularly updated by its developers. The DHS has estimated that each incident involving Emotet costs organizations upwards of $1 million dollars to rectify.
The insurrection at the U.S. Capitol, which saw rioters storm the building and reportedly steal devices belonging to government officials, opened what one cybersecurity expert has called a Pandora’s box of national security and data privacy issues.
New research demonstrates how an adversary in possession of a two-factor authentication (2FA) device can clone it by exploiting an electromagnetic side-channel in the chip embedded in it.