This ransomware steals and encrypts files, demanding ransom for decryption and not releasing stolen data. It is based on the HelloKitty ransomware source code and has been observed in various regions.
The company attributed the infection to software adjustments made by developers to reduce boot times, which inadvertently affected network settings and omitted digital signatures.
The technique works with identity providers like Microsoft Entra ID and can enable attackers to access applications by forging SAML responses with compromised private keys.
The BlackCat/ALPHV ransomware gang claimed responsibility for a cyberattack on Optum, affecting the Change Healthcare platform and potentially compromising sensitive data of millions of individuals and organizations.
The adversary used a PDF file posing as an invitation from the Ambassador of India to a wine-tasting event, which contained a malicious link leading to the WINELOADER malware.
LockBit has set up new data leak and negotiation sites, and is actively recruiting experienced pentesters to join their operation, indicating a potential increase in future attacks.
The model’s payload grants the attacker a shell on the compromised machine, enabling them to gain full control over victims’ machines through what is commonly referred to as a “backdoor”.
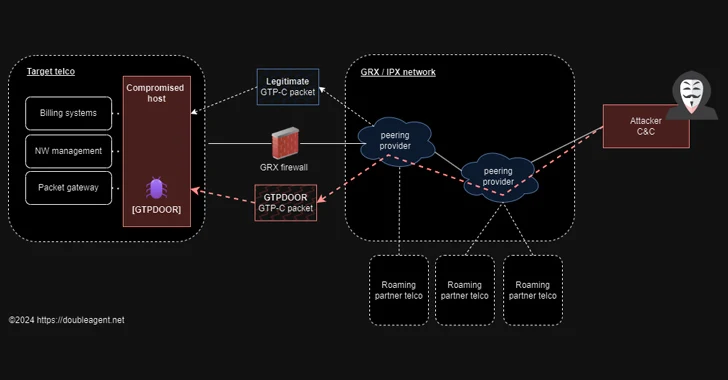
GTPDOOR is a new Linux malware designed for telecom networks that leverages the GPRS Tunnelling Protocol (GTP) for command-and-control communications, posing a threat to subscriber information and call metadata.
Senator Edward Markey has called for an investigation into the data privacy practices of the automotive industry, urging Federal Trade Commission (FTC) Chair Lina Khan to take action.
The attack involves the automated forking of legitimate repositories, resulting in millions of malicious forks with names identical to the original ones, making detection and removal challenging for GitHub.