The U.S. Cybersecurity and Infrastructure Security Agency (CISA), along with the Environmental Protection Agency (EPA) and the FBI, has issued a warning about increased cyberthreats targeting water and wastewater systems.
The incident is suspected to be linked to the outsourcing of IT and HR services to Civica through the East Kent Services partnership, raising concerns about the potential impact on data and services.
The agency’s Joint Cyber Defense Collaborative gathers information to alert potential ransomware victims early on. CISA also assisted a Fortune 500 company and a mass transit operator in preventing significant ransomware attacks.
Subway’s internal system, containing hundreds of gigabytes of data, has allegedly been compromised by the ransomware group. The group has given Subway a deadline to protect the stolen data, and it is currently unknown what ransom they have demanded.
The breach was facilitated by a password spray attack on a non-production test tenant account lacking two-factor authentication, highlighting the importance of robust account security measures.
Suspicions have been raised about a potential data leak from mobile service providers or a breach in the SMS provider used for OTP code delivery as the possible cause of the hacks.
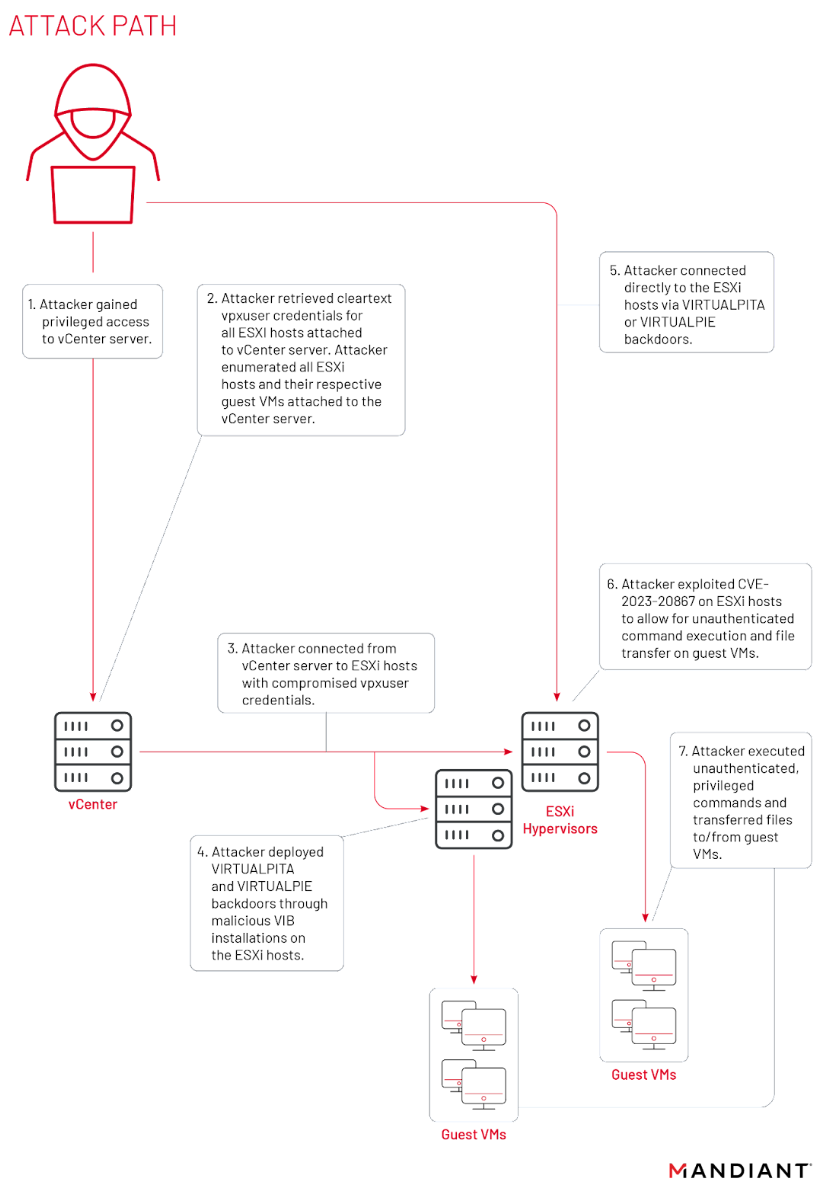
The vulnerabilities allow threat actors to execute arbitrary commands, move laterally, perform data exfiltration, and establish persistent system access, potentially compromising target information systems.
Mandiant researchers observed UNC3886 exploiting a VMware ESXi zero-day vulnerability in June 2023, using novel malware persistence techniques to achieve administrative access within VMware ESXi Hypervisors.
The CISA and the FBI issued a joint warning about the Androxgh0st malware botnet, indicating that threat actors are building a botnet network to extract cloud credentials. Threat actors were also observed using stolen AWS credentials to create new users and user policies on a vulnerable website. The agencies have released IOCs associated with the Androxgh0st […]
A critical vCenter Server vulnerability (CVE-2023-34048) is actively being exploited, allowing attackers to execute remote code with high impact and without requiring authentication.