Chinese APT group Stately Taurus exploited Visual Studio Code to target government entities in Southeast Asia for cyberespionage. They utilized the software’s reverse shell feature to infiltrate networks, a technique first detected in 2023.
TIDrone, linked to Chinese-speaking groups, deploys advanced malware through ERP software or remote desktop tools. Trend Micro identified the threat actor as actively pursuing military and satellite industrial supply chains in Taiwan.
The underground market for malicious large language models (LLMs) is thriving, according to researchers from Indiana University Bloomington. They found 212 malicious LLMs for sale from April through September 2024.
Marsh McLennan and Zurich Insurance Group have issued a white paper highlighting the need for a public-private partnership to help close this significant coverage gap, which poses a threat to both businesses and the economy.
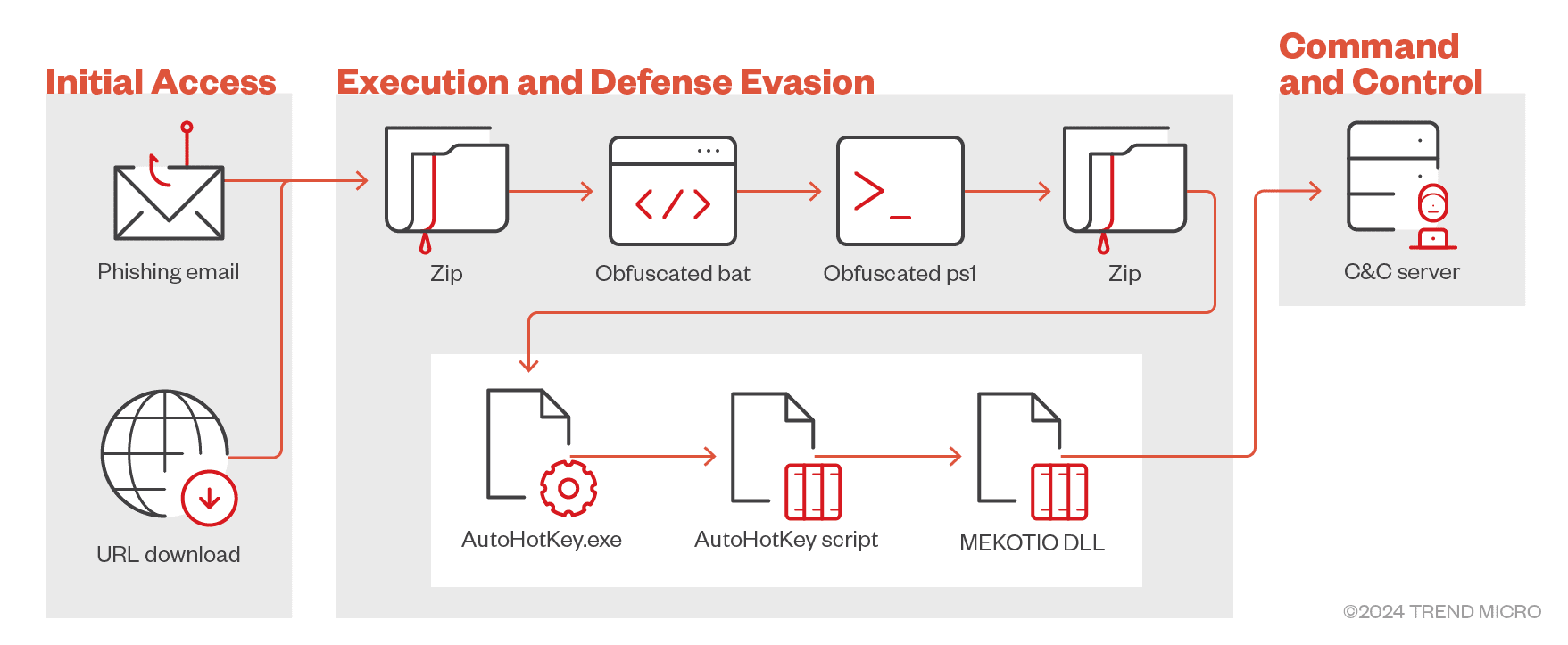
These campaigns aim to steal sensitive banking credentials using innovative tactics, expanding beyond traditional regions like Brazil and Argentina to industries such as manufacturing, retail, and financial services.
Spyware vendors have developed a complex ecosystem that enables them to evade sanctions effectively by utilizing a network of interconnected entities across various jurisdictions.
The attack involves malware manipulating the computer’s RAM to emit controlled electromagnetic radiation that can transmit data to nearby recipients. The attack, created by Israeli researchers, leverages memory access patterns to modulate the RAM.
A couple of critical vulnerabilities in Kibana, tracked as CVE-2024-37288 and CVE-2024-37285, can lead to arbitrary code execution. Elastic urges an immediate update to version 8.15.1.
A new sextortion scam variant is targeting spouses by claiming their partner is cheating on them and providing alleged proof in emails. These scams involve threatening to share compromising images or videos unless a payment is made.
This flaw in the HTTP/2 multiplexer can lead to an endless loop, system crashes, and remote denial-of-service attacks, with a CVSS score of 7. 5. The vulnerability impacts HAProxy Enterprise, ALOHA, and Kubernetes Ingress Controller products.