Ardent proactively took its network offline, suspending all user access. Some facilities are rescheduling non-emergent, elective procedures and diverting some emergency room patients to other area hospitals until systems are back online.
The Daixin Team group added NTMWD to the list of victims on its Tor leak site. The gang claims to have stolen a huge amount of sensitive data from the company and threatens to publish it.
All 17,000 user accounts and characters have been lost in this hack. BUT We will personally, manually restore every item, level, title, pet, etc. that was lost during this event when the servers are back up.
Rivers Casino Des Plaines is the most profitable casino in the state of Illinois. Currently, there is no information on who is behind the attack. The number of people potentially affected by the breach is also unknown.
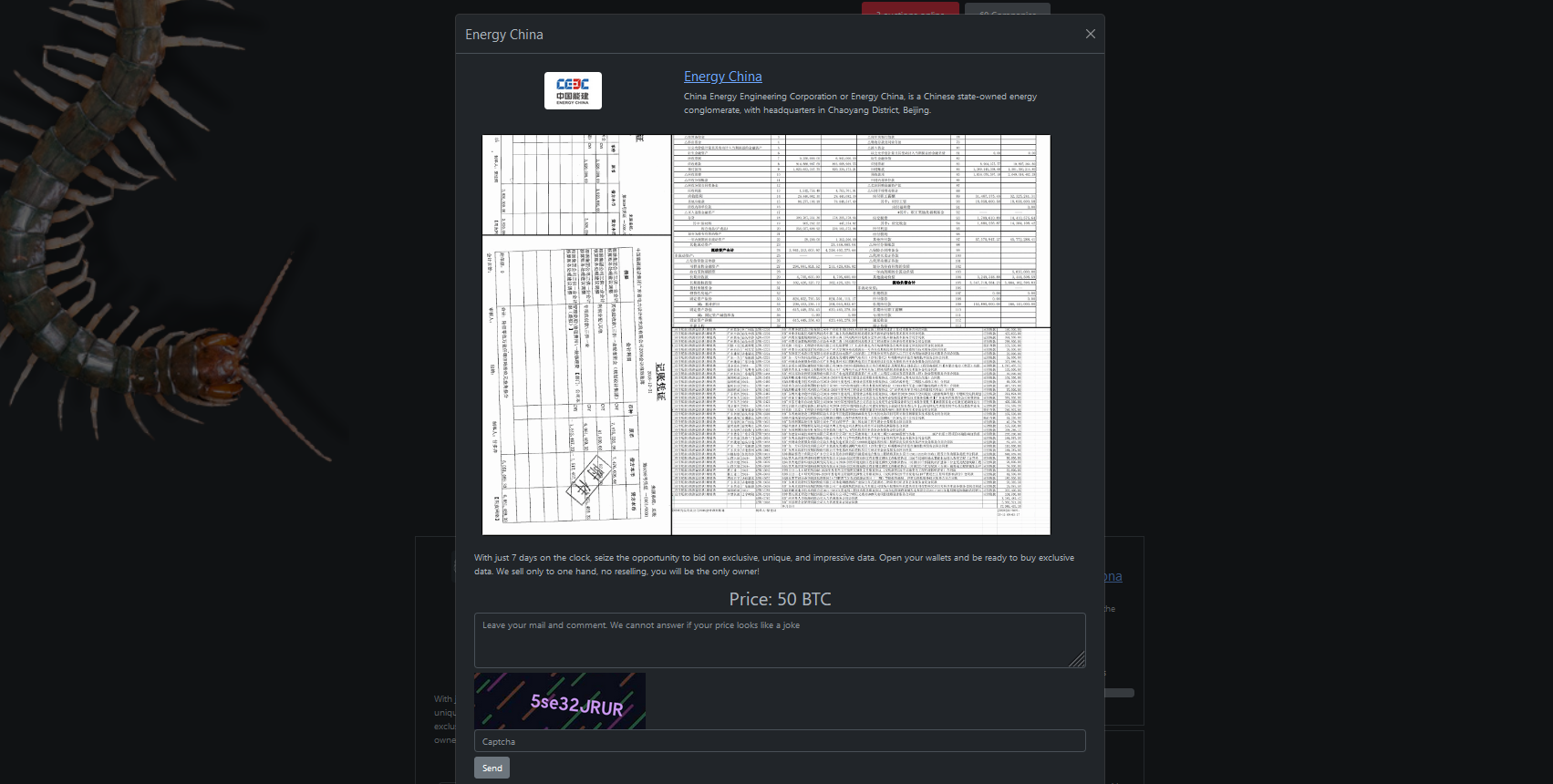
The ransomware group claims to have stolen a substantial trove of ‘impressive data’ and is auctioning it for 50 BTC. The gang announced to publicly release the data over the seven days following the announcement.
The hospital’s IT team is working to determine the impact of the outage and restore access to the network. Meanwhile, the healthcare provider is following established downtime protocols, revealed a spokesperson for Portneuf Medical Center.
The machine that was hacked uses a system called Unitronics, which contains software or has components that are Israeli-owned. The system has since been disabled. Authorities stressed that there is no known risk to the drinking water or water supply.
The NCSC and South Korea’s NIS issued a joint warning against the Lazarus hacking group leveraging a zero-day flaw in the MagicLine4NX software. The zero-day exploit allowed Lazarus to conduct a series of supply-chain attacks, starting with a watering hole attack on a media outlet’s website. Organizations using a vulnerable version of MagicLine4NX must update […]
The attack chain involves the PAExec remote administration tool, an alternative to PsExec that’s used as a launchpad to create a scheduled task that masquerades as ‘MicrosoftsUpdate’ which subsequently is configured to execute a Windows batch script.
The company is now trying to recover the funds but argued that the incident “stands out as one of the most sophisticated in the history of DeFi.” The company advised users to “promptly withdraw their funds.”