BulletProofLink offered ready-to-use phishing templates to conduct credential harvesting campaigns, targeting well-known services and engaging in double theft to maximize profits.
They have created fake skills assessment portals to trick recruiters into registering for an account. Previously, they used platforms like LinkedIn and employed lures related to skills assessment.
CherryBlos is a family of Android malware that can steal cryptocurrency by extracting sensitive information from photos on a user’s phone. This includes details related to cryptocurrency wallets, such as recovery phrases.
The industries most frequently targeted by Asian APT groups include government, industrial, healthcare, IT, agriculture, and energy sectors, emphasizing the importance of tailored security measures for these industries.
Cisco’s Talos Intelligence blog reveals a sophisticated spam exploit using Google Forms’ quiz results feature, collecting email addresses subtly via a quiz template. The spammer leverages Google’s infrastructure to send phishing emails, bypassing spam blockers until Google addresses this method, ultimately leading victims to a complex cryptocurrency scam. As these types of scams continue to […]
The attackers are targeting healthcare organizations in the U.S. using local ScreenConnect instances used by Transaction Data Systems (TDS), a pharmacy supply chain and management systems solution provider.
Attackers exploited the CVE-2023-22515 vulnerability to gain initial access and embed a web shell, allowing them to execute malicious actions without needing a valid user account.
The hospital has taken its information systems offline and is working with cybersecurity specialists and law enforcement to restore functionality, but it is unclear if a ransom has been demanded or if patient data has been compromised.
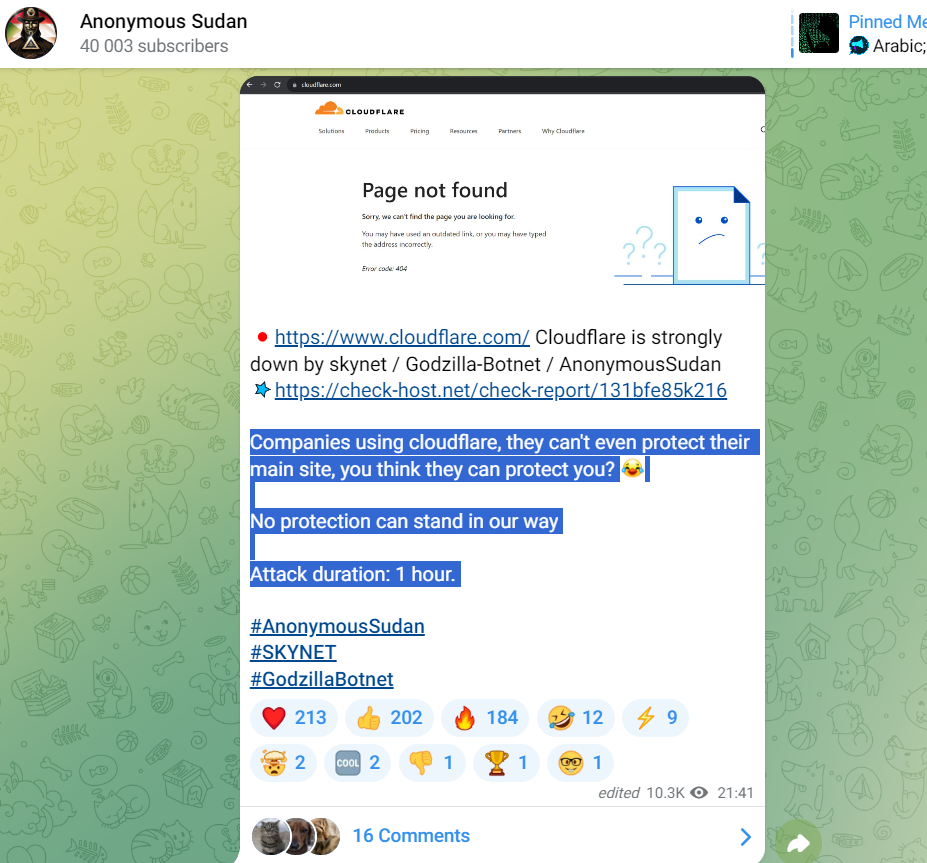
The attack caused intermittent connectivity issues for a few minutes but did not impact any services or products provided by Cloudflare. The group claims to have used the Skynet and Godzilla botnets for the recent attacks.
The spyware, disguised as an Android app, has been available on the website since January 2023 and has compromised at least 20 mobile devices, harvesting sensitive information and uploading it to a command-and-control server.