Attackers redirect victims to scams that involve QR codes and phishing websites promising to double their cryptocurrency investments, often using deep fake videos of Elon Musk to add credibility.
Stream-jacking attacks on YouTube are increasing, targeting popular channels to spread deceptive content. Cybercriminals hijack these channels, often impersonating famous figures or brands like Elon Musk and Tesla, promoting scams like crypto doubling. Viewers should be cautious of videos with clickbait titles, especially those promoting financial opportunities.
Really Simple Systems exposed a non-password-protected database with over 3 million records, including highly sensitive customer information such as medical records and tax documents.
Despite the focus on cloud security, many organizations still have risk management lapses, such as not addressing disaster recovery and backup with their cloud service provider.
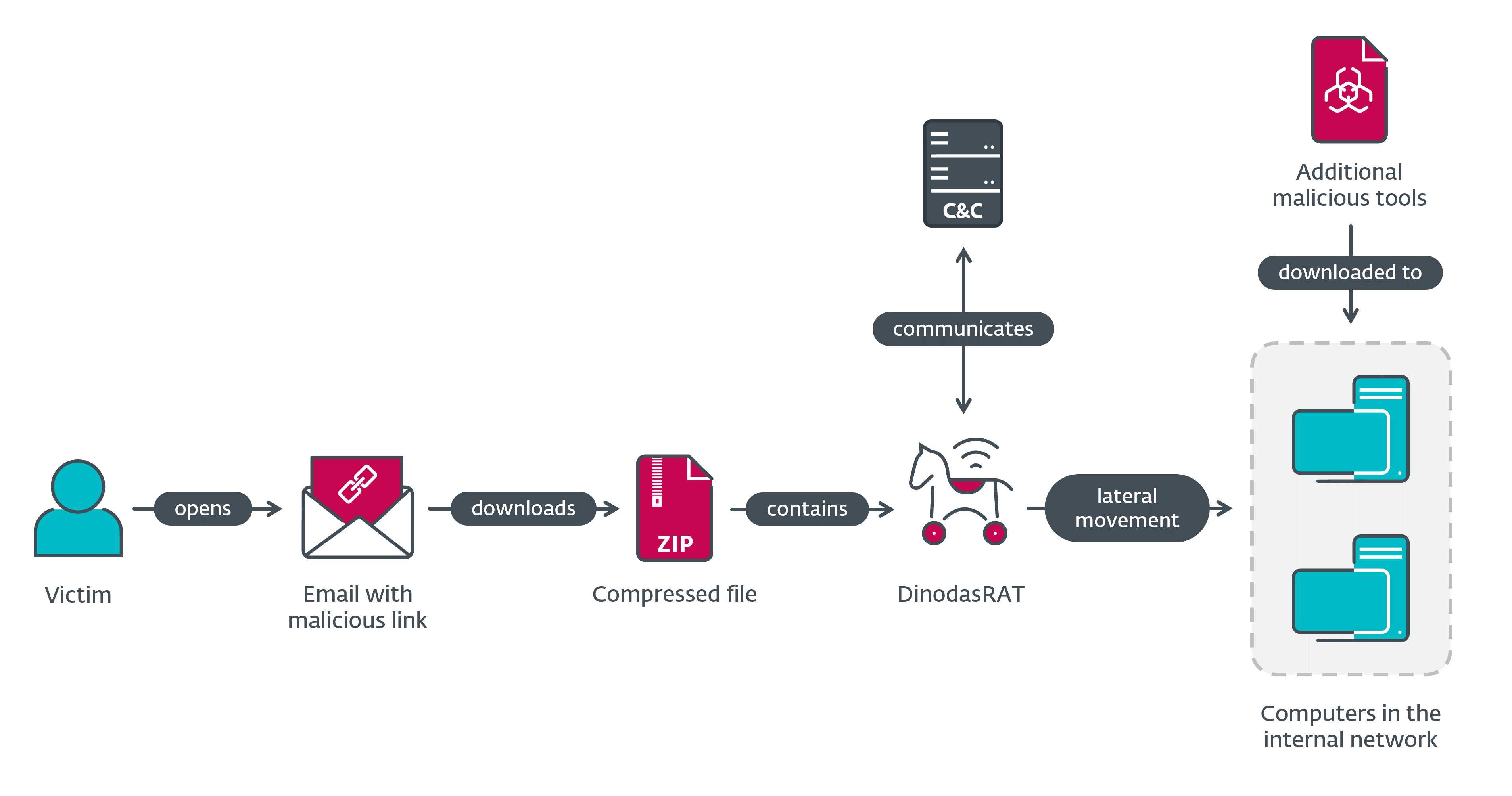
While the specific APT group behind the campaign could not be identified, there is medium confidence that it is a China-aligned threat group based on the use of a variant of Korplug, which is commonly associated with such groups.
Dubbed “WebWyrm” by CloudSEK, the operation has already targeted more than 100,000 individuals across over 50 countries by impersonating over 1000 companies across 10 industries. It has already potentially netted the scammers over $100m.
South Korea’s National Intelligence Service said it is notifying shipbuilders of threats to their systems and networks and advising major shipyards to conduct independent security audits to plug security holes in digital infrastructure.
According to some experts, the proposed EU mandate for software publishers to disclose zero-day exploits within 24 hours risks compromising cybersecurity efforts by giving government agencies access to a real-time database of vulnerabilities.
The Snatch cybercrime group has been using paid Google ads to distribute their malware, posing as trusted software like Adobe Reader, Discord, Microsoft Teams, and Mozilla Thunderbird.
The breach was discovered on May 31, 2023, and unauthorized actors were able to access Arietis Health’s MOVEit server, potentially acquiring confidential files belonging to patients at NorthStar Anesthesia.