The Exim maintainers and the Zero Day Initiative (ZDI) have experienced delays and communication issues in addressing these vulnerabilities, raising concerns about the handling of security flaws in widely used software.
The FBI warns that changes in the global energy supply, including US exports of liquefied natural gas and shifts in the crude oil supply chain, are likely to boost the targeting of critical energy infrastructure by Chinese and Russian hackers.
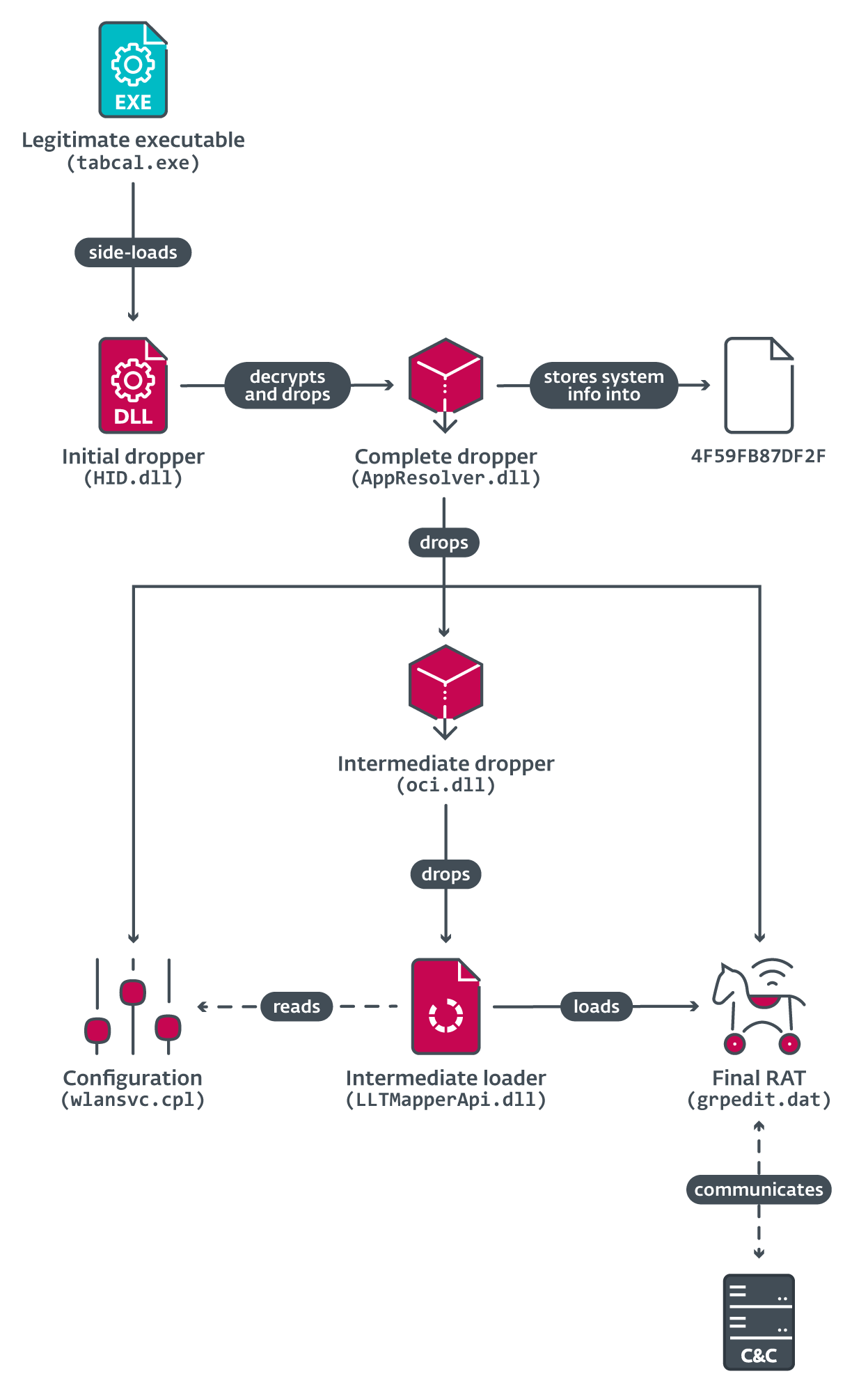
The Menorah malware is designed for cyberespionage and possesses capabilities such as machine identification, file reading and uploading, shell command execution, and file downloading.
The flaw, tracked as CVE-2018-14667, was added by CISA on Thursday to its Known Exploited Vulnerabilities (KEV) Catalog, with federal agencies being instructed to apply mitigations or discontinue the use of the product by October 19.
The payment, intended for a new police headquarters building, was made to a scammer who posed as the legitimate contractor, Moss Construction. The incident underscores the need for increased cybersecurity measures against business email compromise.
Government-issued devices face heightened security risks during a federal shutdown, as furloughed employees are typically restricted from using them, leaving networks and devices vulnerable.
The attack involved the deployment of a sophisticated backdoor called LightlessCan, which mimics native Windows commands and implements techniques to avoid detection by security monitoring software.
As part of this trend, which was observed in July 2023, the FBI notes in a new private industry notification, threat actors deploy two ransomware variants in close date proximity to one another.
By synthesizing data from various security sources and utilizing natural language commands, Nexusflow aims to revolutionize cybersecurity operations by seamlessly interpreting human instructions and providing insights.
“The impact of this vulnerability is severe, as it grants attackers the ability to gain unauthorized access to systems, exfiltrate sensitive data, and execute malicious code remotely,” Cyfirma notes in an analysis of the bug and its exploitation.