The CISA has added new vulnerabilities to its Known Exploited Vulnerabilities catalog, including Dahua IP Camera authentication bypass flaws, a Linux Kernel buffer overflow issue, and a Microsoft Exchange Server vulnerability.
Liverpool fans have suffered the most in Premier League ticket scams for the 2023/24 season, losing over £17,000 (~$22,460) to criminals, as revealed by a report from NatWest Bank. Arsenal supporters were also hit hard, losing £12,000 (~$15,855).
Greasy Opal, a well-known developer, has been aiding cybercriminals for 16 years by offering a tool that can solve CAPTCHAs automatically on a large scale, bypassing security measures.
The urgent security update, Microsoft Edge Stable Channel Version 128.0.2739.42, based on Chromium versions 128.0.6613.85 and 128.0.6613.84, addresses a total of 25 security issues.
Slack fixed a vulnerability in its AI feature that could allow attackers to steal data from private channels. The flaw involved a prompt injection flaw in an AI feature, which allowed attackers to manipulate the system to perform malicious actions.
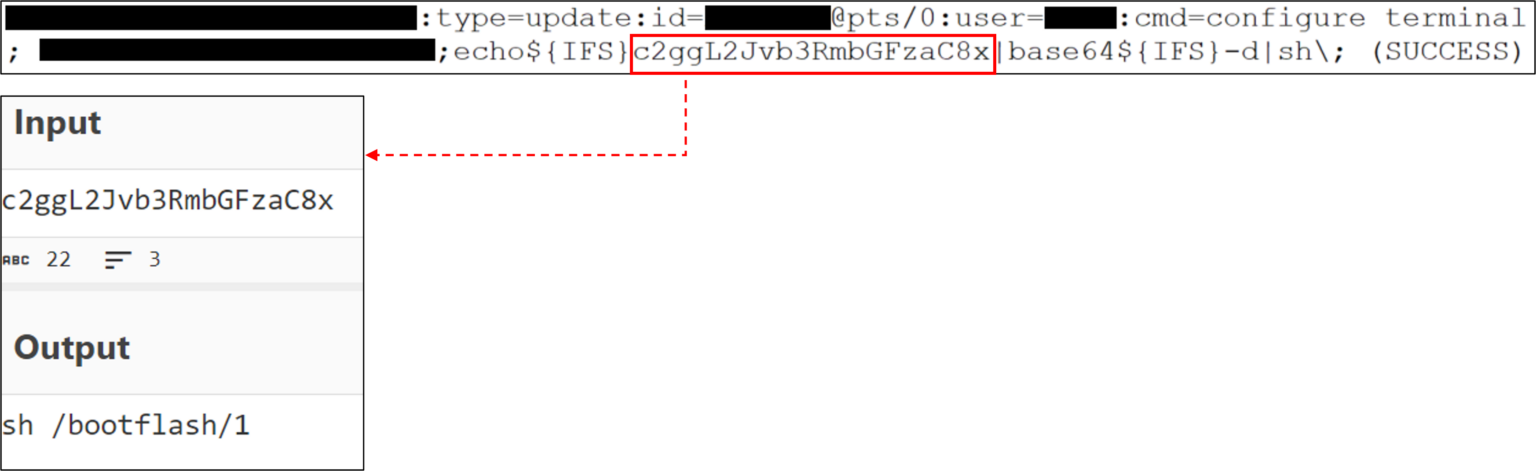
The China-linked APT group Velvet Ant exploited a zero-day vulnerability in Cisco switches, CVE-2024-20399, to take control of network devices. The flaw in Cisco NX-OS Software’s CLI enabled attackers with Admin credentials to run arbitrary commands.
DataDome researchers found that major UK political parties lack critical security features to protect against bot and credential stuffing attacks on their donation platforms.
Hackers are now using AppDomain Injection to drop Cobalt Strike beacons in a series of attacks that began in July 2024. This technique, known as AppDomain Manager Injection, can weaponize any Microsoft .NET application on Windows.
This vulnerability allows local attackers to escalate privileges to SYSTEM level through a heap-based buffer overflow. With a CVSS score of 7.8, CVE-2024-38054 is a critical flaw patched by Microsoft in July.
Exploiting this flaw, attackers can manipulate daemonsets, create service account tokens, and impersonate high-privilege accounts like cluster-admin. This could lead to a complete cluster takeover.