Researchers from the Technical University of Berlin have developed a method to jailbreak the AMD-based infotainment systems used in all recent Tesla car models and make it run any software they choose.
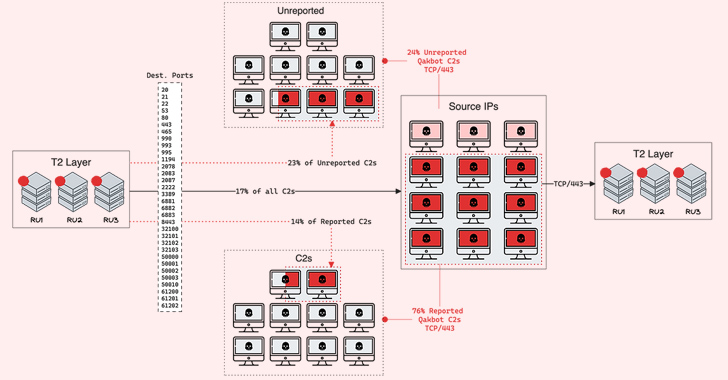
A majority of the bot C2 servers, which communicate with the victim hosts, are located in India and the U.S. Destination IP addresses identified from outbound T2 connections are primarily based in the U.S., India, Mexico, and Venezuela.
According to the California Privacy Protection Agency, cars are “connected computers on wheels” and should be treated as such. It recently announced its enforcement division will review the data privacy practices of connected vehicle manufacturers.
The vulnerability, known as Downfall, exploits a technique used to increase performance in the x86 architecture. By sharing a small register buffer, different applications can inadvertently leave data that can be accessed by an attacker.
Authorities are sounding the alarm about double-extortion attacks against healthcare and public health sector organizations by a relatively new ransomware-as-a-service group, Rhysida, which until recently had mainly focused on other industries.
The Cybersecurity Strategic Plan for fiscal years 2024-2026 outlines the agency’s plans for achieving a future where damaging cyberattacks are rare, organizations are resilient, and technology is secure by design.
The phishing operation, originating from Russia but pretending to be Ukrainian, utilized a high-quality single-page application to create convincing websites and steal credit card and bank details.
Interestingly, the analysis also revealed that malicious attacks such as malware, phishing, and ransomware accounted for just a third (33%) of breaches reported to the ICO, versus 40% of incidents caused by insider threats.
A recent investigation by cybersecurity firm SentinelLabs has revealed that North Korean hackers have targeted a Russian missile engineering organization called NPO Mashinostroyeniya.
The State and Local Cybersecurity Grant Program (SLCGP), now in its second year, is a $1 billion fund with allocations spanning four years and specifically targeting state, local, and territorial government cyber resilience efforts.