The assessment, which GAO began at the end of last year, also found that many State Department posts lack not only a chief information security officer, but any cybersecurity personnel whatsoever.
Potential victims who click on the provided links are redirected to phishing websites masquerading as legitimate extensions of specific NFT projects. Scammers go to great lengths to replicate the appearance and user experience of real NFT platforms.
The files and directories targeted by the malicious code could potentially contain developers’ sensitive data. Researchers speculate the packages are part of a highly-targeted attack on developers working in the cryptocurrency sector.
“Campaigns using versioning commonly target users’ credentials, data, and finances,” Google Cybersecurity Action Team (GCAT) said in its August 2023 Threat Horizons Report shared with The Hacker News.
The database, hosted on Oracle’s cloud and more than 1.7 terabytes in size at the time it was exposed, contained customer’s personal information, including names, gender, dates of birth, home addresses, flight information and passport numbers.
The personal information compromised in the attack includes any combination of the following: name, U.S. Social Security Number, date of birth, home mailing address, Serco and/or personal e-mail address, and selected health benefits for the year.
The National Science Foundation’s NOIRLab did not respond to requests for comment but published a notice on Tuesday night explaining that the lab had discovered an attempted cyberattack on its systems that morning.
A rather sophisticated version of the Rilide malware was identified targeting Chromium-based web browsers to steal sensitive data and cryptocurrency. Experts identified over 1,300 phishing websites distributing the new version of Rilide Stealer along with other harmful malware such as Bumblebee, IcedID, and Phorpiex. Organizations need to leverage the IOCs to understand the nature and attack scope […]
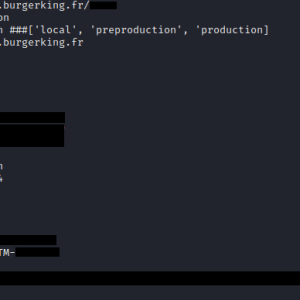
On June 1st, 2023, the Cybernews research team discovered a publicly accessible environment file (.env) belonging to Burger King’s French website, containing various credentials. The file was hosted on the subdomain used for posting job offers.
The list of LOLBAS files – legitimate binaries and scripts present in Windows that can be abused for malicious purposes, will soon include the main executables for Microsoft’s Outlook email client and Access database management system.