MoonPeak is an evolved form of the Xeno RAT malware previously used by North Korean actors and is capable of loading plugins, launching processes, and communicating with a command-and-control (C2) server.
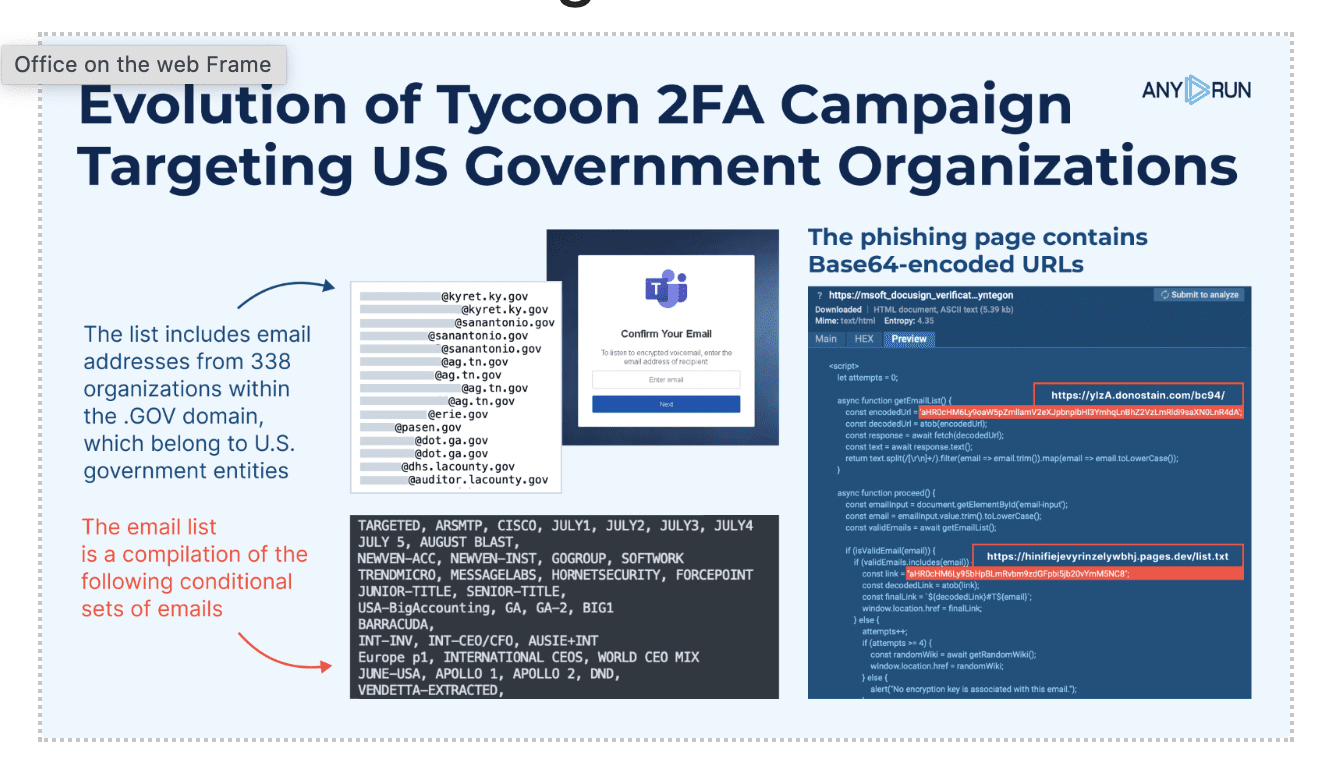
The attackers have become more sophisticated in their approach, specifically targeting email addresses from 338 US government entities. The phishing links redirect victims to a fake Microsoft Teams login page.
The HYAS Threat Intelligence team has detected threat actors using Steam for malicious activities, like hosting C2 domain addresses and exploiting user accounts. One actor used a Substitution Cipher to hide C2 domains.
The flaw, tracked as CVE-2024-38206, allows an authenticated attacker to bypass SSRF protection and leak information over a network. A researcher at Tenable discovered the vulnerability, which exploits Copilot’s ability to make external web requests.
A PoC exploit has been released for a critical vulnerability (CVE-2024-41992) found in the Arcadyan FMIMG51AX000J model, as well as other devices using the same firmware version.
The suspicious ad for Slack appeared legitimate but was likely malicious. Clicking on it would initially redirect to slack.com. However, after several days, it started redirecting to a click tracker, showing signs of a potentially malicious campaign.
This latest Log4j exploitation-based attack uses obfuscated LDAP requests to evade detection and executes malicious scripts, establishing persistence and exfiltrating data through encrypted channels.
Researchers from Quarkslab found a hardware backdoor in the FM11RF08S RFID cards manufactured by Shanghai Fudan Microelectronics, enabling attackers to compromise user-defined keys within minutes.
In these file-sharing phishing attacks, cybercriminals impersonate colleagues or trusted services to trick targets into clicking on malicious links that can lead to data theft or malware infection.
The vulnerability allows attackers to inject malicious content into annotations, leading to arbitrary command injection and potential access to controller credentials, enabling full access to cluster secrets.