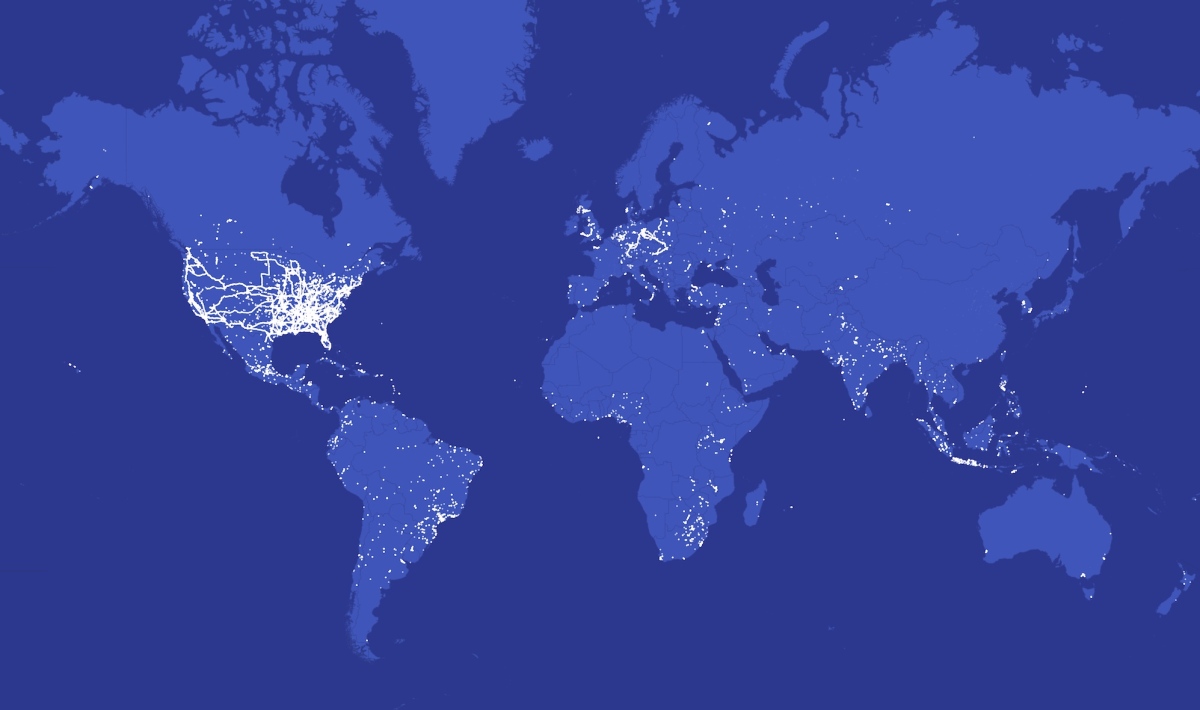
Spyhide is secretly collecting private data from tens of thousands of Android devices worldwide. The app is often installed on a victim’s phone by someone who knows their passcode, and it remains hidden on the home screen.
“They are still heavily focused on Latin American financial institutions, but the changes in their techniques represent a significant risk to multi-regional financial organizations as well,” Sygnia said in a statement shared with The Hacker News.
Mandiant’s investigation into the attack now revealed that the intrusions were attributed to UNC4899, a hacking group associated with the Democratic People’s Republic of Korea (DPRK).
The allegation, made on the hacker forum Popürler, was observed by cyber threat intelligence provider SOCRadar and dark web monitoring firm Falcon Feeds on July 25, 2023.
Thales will buy Imperva for an enterprise value of $3.6 billion ($3.7 billion gross value minus $0.1 billion tax benefits). The transaction is expected to close by the beginning of 2024.
A China-linked group APT31 (aka Zirconium) has been linked to a cyberespionage campaign targeting industrial organizations in Eastern Europe. The attackers abused DLL hijacking vulnerabilities in cloud-based data storage systems such as Dropbox or Yandex, as well as a temporary file-sharing service, to deliver next-stage malware.
The issues, discovered by Midnight Blue in 2021 and held back until now, have been collectively called TETRA:BURST. There is no conclusive evidence to determine that the vulnerabilities have been exploited in the wild to date.
In the second quarter of 2023, GuidePoint Research and Intelligence Team (GRIT) tracked 1,177 total publicly posted ransomware victims claimed by 41 different threat groups.
The most severe of these issues, tracked as CVE-2023-22508 (CVSS score of 8.5), was introduced in Confluence version 7.4.0. The second bug, tracked as CVE-2023-22505 (CVSS score of 8.0), was introduced in Confluence version 8.0.0.
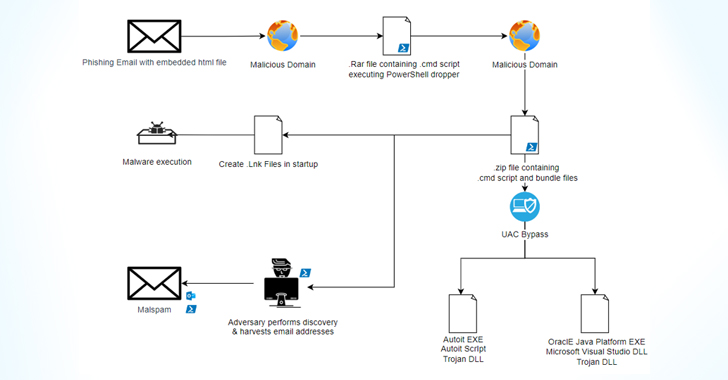
ASEC discovered that the North Korean state-sponsored Lazarus APT group is attacking Windows Internet Information Service (IIS) web servers and using them to distribute malware. It is imperative for organizations to adopt stringent measures, including attack surface management, to identify exposed assets and continuously apply the latest security patches.