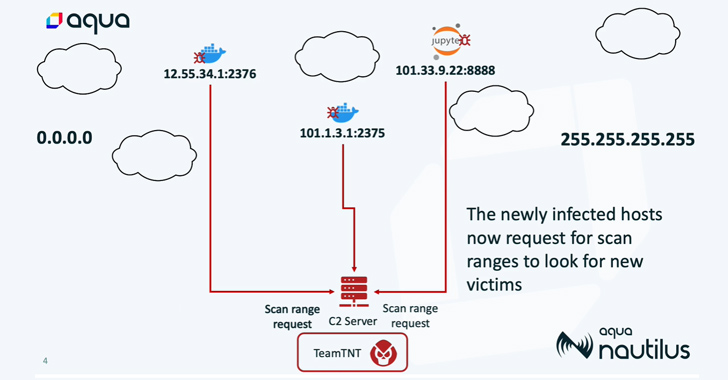
“The botnet run by TeamTNT has set its sights on Docker and Kubernetes environments, Redis servers, Postgres databases, Hadoop clusters, Tomcat and Nginx servers, Weave Scope, SSH, and Jupyter applications,” Aqua security researchers said.
A majority of the infections are located in the U.K. and the U.S., followed by Argentina, Nigeria, Brazil, Italy, Bangladesh, Vietnam, India, Russia, and South Africa, among others.
It was discovered that AIOS version 5.1.9 writes plaintext passwords from login attempts to the database, which essentially provides any privileged user with access to the login credentials of all other administrator users.
The BlackLotus source code that was published on GitHub on Wednesday has been stripped of the ‘Baton Drop’ exploit targeting CVE-2022-21894, and uses the bootlicker UEFI firmware rootkit, but contains the rest of the original code.
The inclusion of the four vulnerabilities — CVE-2023-32046, CVE-2023-32049, CVE-2023-35311, and CVE-2023-36874 — into CISA’s catalog means the bugs are already being exploited by hackers.
The Cisco SD-WAN vManage management software is impacted by a flaw that allows an unauthenticated, remote attacker to gain read or limited write permissions to the configuration of the affected instance.
With a recent $50 million Series C funding round led by Paladin Capital Group, Secure Code Warrior plans to improve its platform and expand its workforce to meet the growing demand for cybersecurity skills training.
Multiple hardcoded credentials found on the Technicolor TG670 DSL gateway router allow attackers to completely take over devices, the CERT Coordination Center (CERT/CC) warns.
The NRC said it immediately suspended the database to protect the data and prevent further attacks. They also launched an external forensic investigation to determine the scope and impact of the cyberattack.
Comparitech analyzed 225 confirmed cyberattacks on the sector over the past five years and found that the average organization loses two weeks in downtime due to an incident.