A new version of the Common Vulnerability Scoring System (CVSS 4.0) has been unveiled publicly by the Forum of Incident Response and Security Teams (FIRST) on July 13, 2023.
The flaw is tracked as CVE-2023-36664, having a CVSS v3 rating of 9.8, and impacts all versions of Ghostscript before 10.01.2, which is the latest available version released three weeks ago.
The company published 17 advisories detailing roughly a dozen Junos OS-specific security defects, and nearly three times as many issues in third-party components used in its products.
One of the U.S.’s most popular zoos has been hit with a cyberattack involving the theft of employee and vendor information, and a likely offshoot of the Royal ransomware gang is taking credit.
The Vietnamese threat actors are using malicious Chrome extensions to steal Facebook account credentials, with over 800 victims worldwide and $180K in compromised ad budget.
While overall crypto proceeds, including from crimes such as scams, fell dramatically over the past year, ransomware funds are expected to hit $899 million in 2023, according to Chainalysis.
The 1756 EN2 and 1756 EN3 products are impacted by CVE-2023-3595, a critical flaw that can allow attackers to achieve remote code execution with persistence on targeted systems by using specially crafted Common Industrial Protocol (CIP) messages.
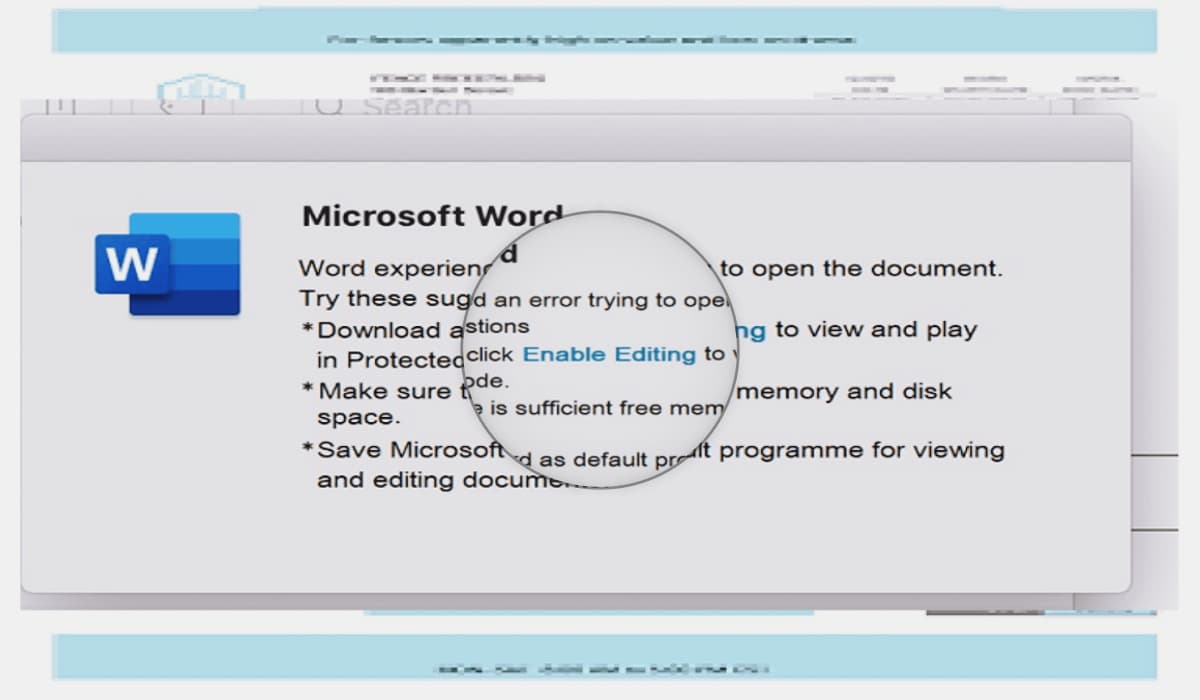
“An attacker could create a specially crafted Microsoft Office document that enables them to perform remote code execution in the context of the victim,” reads the advisory published by Microsoft.
About 39% of businesses experienced a data breach in their cloud environment last year, an increase from the 35% reported in 2022, according to Thales. Human error was reported as the leading cause of cloud data breaches by 55% of those surveyed.
FortiGuard Labs recently uncovered a concerning discovery in their investigation, revealing a series of malicious Microsoft Office documents designed to take advantage of well-known vulnerabilities.