Recently, Microsoft’s Incident Response team investigated several BlackByte 2.0 ransomware attacks and exposed these cyber strikes’ terrifying velocity and damaging nature.
“TA453 eventually used a variety of cloud hosting providers to deliver a novel infection chain that deploys the newly identified PowerShell backdoor GorjolEcho,” Proofpoint said in a new report.
Computer scientists at the University of Waterloo have discovered a method of attack that can successfully bypass voice authentication security systems with up to a 99% success rate after only six tries.
A joint advisory from the CISA, the FBI, the MS-ISAC, and the Canadian Centre for Cyber Security (CCCS) discovered a rise in the use of the Truebot malware by threat actors. Notably, these actors are increasingly exploiting the CVE-2022-31199 flaw to target organizations in the U.S. and Canada with the malware. Organizations are also advised […]
A survey by Malwarebytes revealed that a majority of respondents do not trust the information produced by ChatGPT and believe it poses potential safety and security risks.
The apps, both from the same publisher, can launch without any user interaction to steal sensitive data and send it to servers in China. Despite being reported to Google, the two apps continue to be available in Google Play at the time of publishing.
The threat actors behind the attacks compromised target networks by exploiting a critical remote code execution (RCE) vulnerability in the Netwrix Auditor software tracked as CVE-2022-31199.
A new tool available on GitHub can enable attackers to misuse a recently disclosed vulnerability in Microsoft Teams and automatically deliver malicious files to users’ systems.
“There are indications that the following [vulnerabilities] may be under limited, targeted exploitation,” reads Google’s bulletin, highlighting CVE-2023-26083, CVE-2021-29256, and CVE-2023-2136.
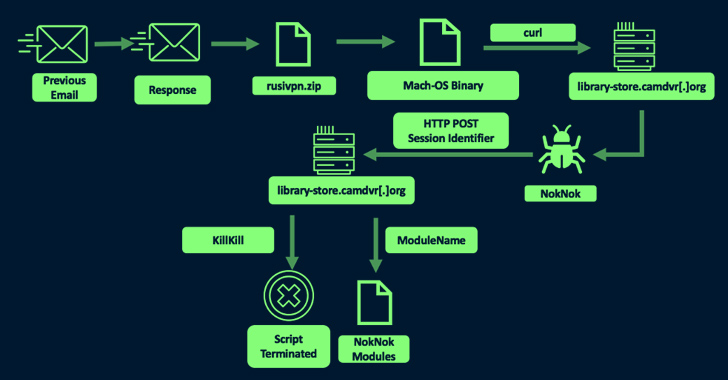
The recent detection of RedEnergy stealer-as-a-ransomware represents an advanced threat that combines stealthy data theft and encryption techniques to cause significant damage and seize control over its targets.