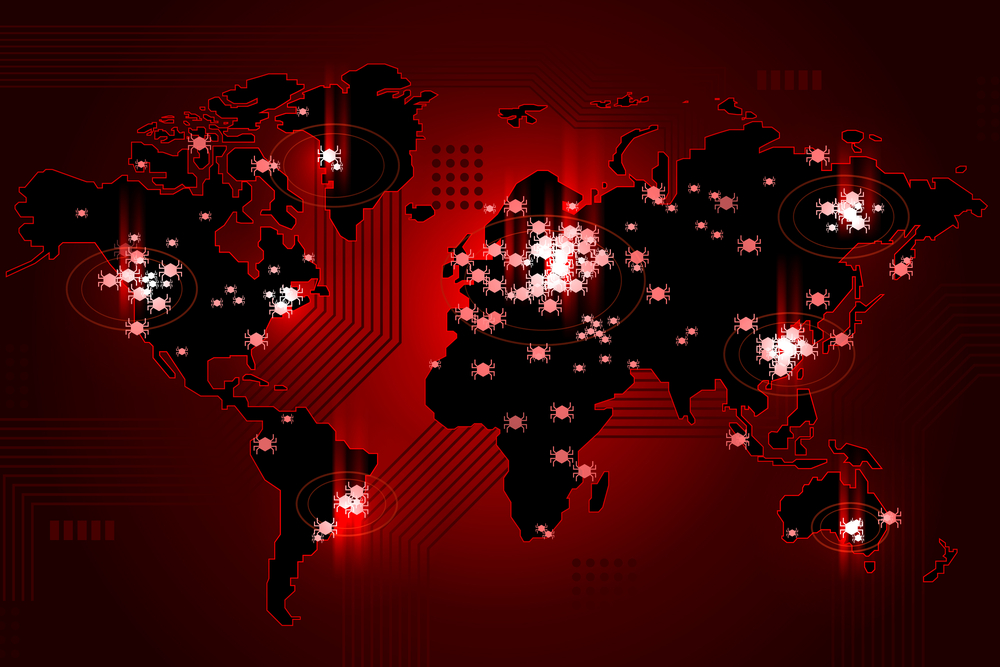
SentinelLabs detected 10 ransomware families employing VMware ESXi lockers, derived from the leaked 2021 Babuk source code. These variants emerged between H2 2022 and H1 2023. The report also highlights similarities between Babuk’s source code and the ESXi encrypters used by Conti and REvil, indicating some connection between them.
The group is swiftly expanding its operations. To date, it has compromised three organizations in the U.S. and one in South Korea across several business verticals, including manufacturing, wealth management, insurance providers, and pharmaceuticals.
The Illinois Department of Healthcare and Family Services (HFS) and Department of Human Services (IDHS) have disclosed a data breach within the State of Illinois Application for Benefits Eligibility (ABE) system’s Manage My Case (MMC) portal.
The targeting of VMware ESXi hypervisors with ransomware to scale such campaigns is a technique known as hypervisor jackpotting. Over the years, the approach has been adopted by several ransomware groups, including Royal.
Although threat actors may not be directly correlating the insurance factor to find targets, a reason for this may be that as insurers require more from companies those able to pay for insurance are also likely to be able to afford bigger ransoms.
PharMerica’s letter does not provide details on the type of cyberattack that it suffered, but it appears that the Money Message ransomware group is responsible for the incident the group started leaking PII and PHI allegedly stolen from PharMerica.
Almost six weeks after the attack was disclosed, Capita warned Universities Superannuation Scheme (USS), the largest private pension scheme in the UK, to react to the incident under the assumption that their members’ data was stolen.
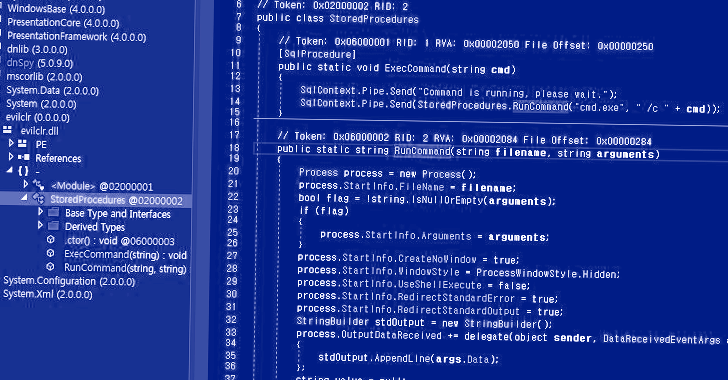
Poorly managed Microsoft SQL (MS SQL) servers are the target of a new campaign that’s designed to propagate a category of malware called CLR SqlShell that ultimately facilitates the deployment of cryptocurrency miners and ransomware.
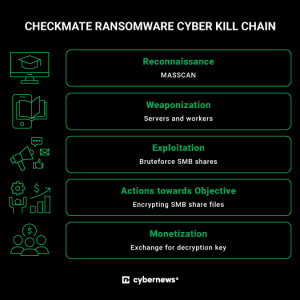
After gaining access to SMB shares, threat actors behind CheckMate ransomware encrypt all files and leave a ransom note demanding payment in exchange for the decryption key.
While this security bug (CVE-2023-25717) was addressed in early February, many owners are likely yet to patch their Wi-Fi access points. Furthermore, no patch is available for those who own end-of-life models affected by this issue.