These guidelines, developed by a group of agencies—including the U.S. CISA, the ACSC, and the U.K NCSC—aim to help communities transitioning into “smart cities” fortify the digital networks crucial to delivering basic utilities and services.
Some ISAs include built-in security features to mitigate vulnerabilities and attacks, such as hardware-based encryption, memory protection, and data execution prevention.
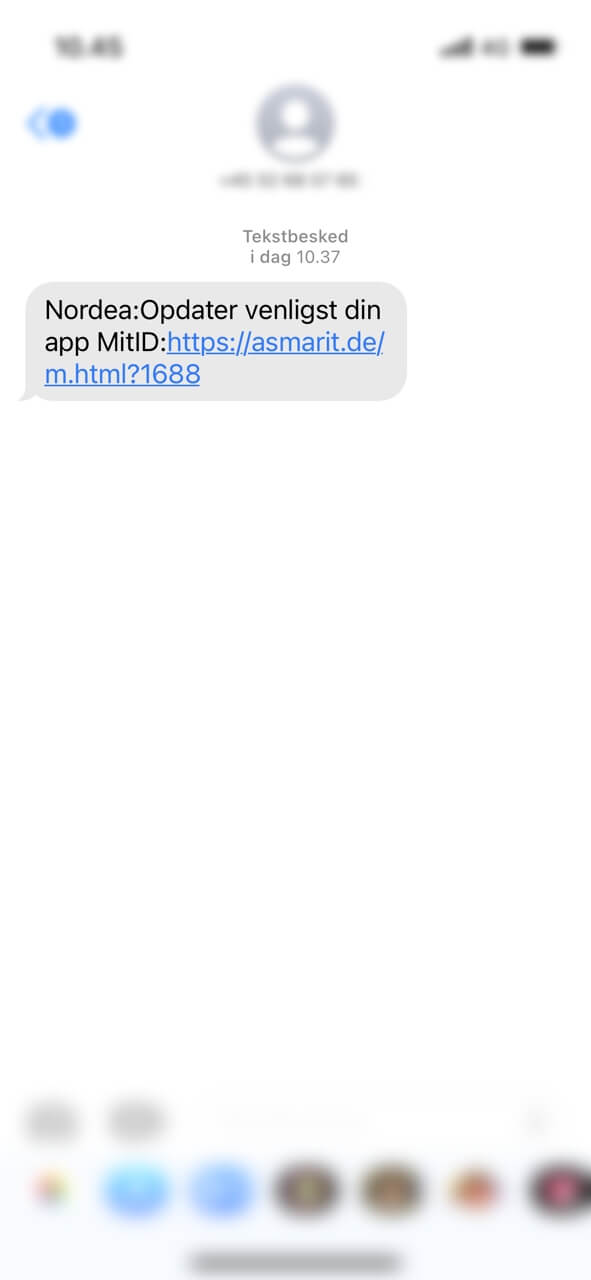
The data analyzed so far suggests that the threat actor takes advantage of the MitID authentication mechanism in order to redirect the customer to a fake webpage for various malicious actions on target.
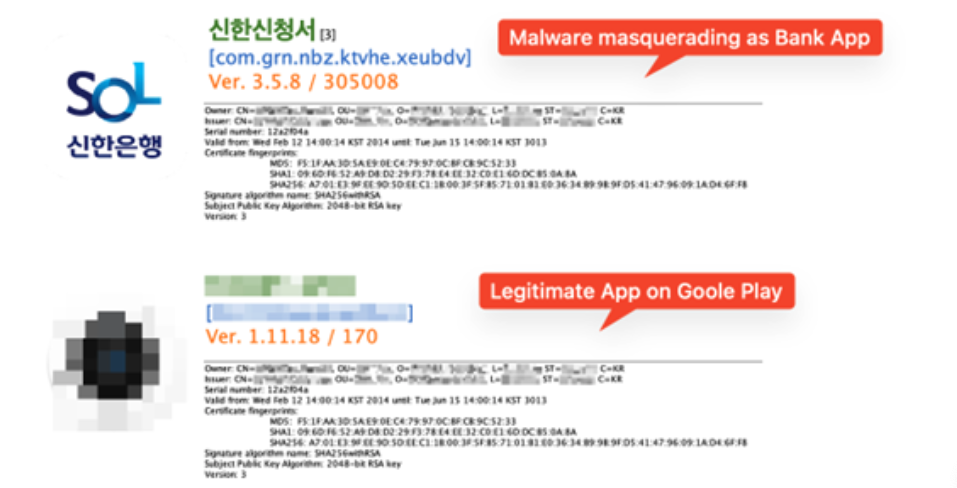
This threat had been disclosed to the company that owns the legitimate key last year and the company has taken precautions. The company confirmed that they have replaced the signing key and currently, all their apps are signed with a new singing key.
Foreseeing every possible twist and turn of a breach may be impossible, but through extensive wargaming, security teams can simulate diverse situations to give them a proactive edge.
Google’s Cybersecurity Action Team (GCAT) and Mandiant researched a list of techniques and methods used by threat actors over the period for penetrating the environments and other malicious activities.
Experts say insurance companies’ demand for stronger cybersecurity practices from policyholders contributed toward fewer ransomware claims and decelerating premiums in 2022.
The AuKill tool abuses an outdated version of the driver used by version 16.32 of the Microsoft utility, Process Explorer, to disable EDR processes before deploying either a backdoor or ransomware on the target system.
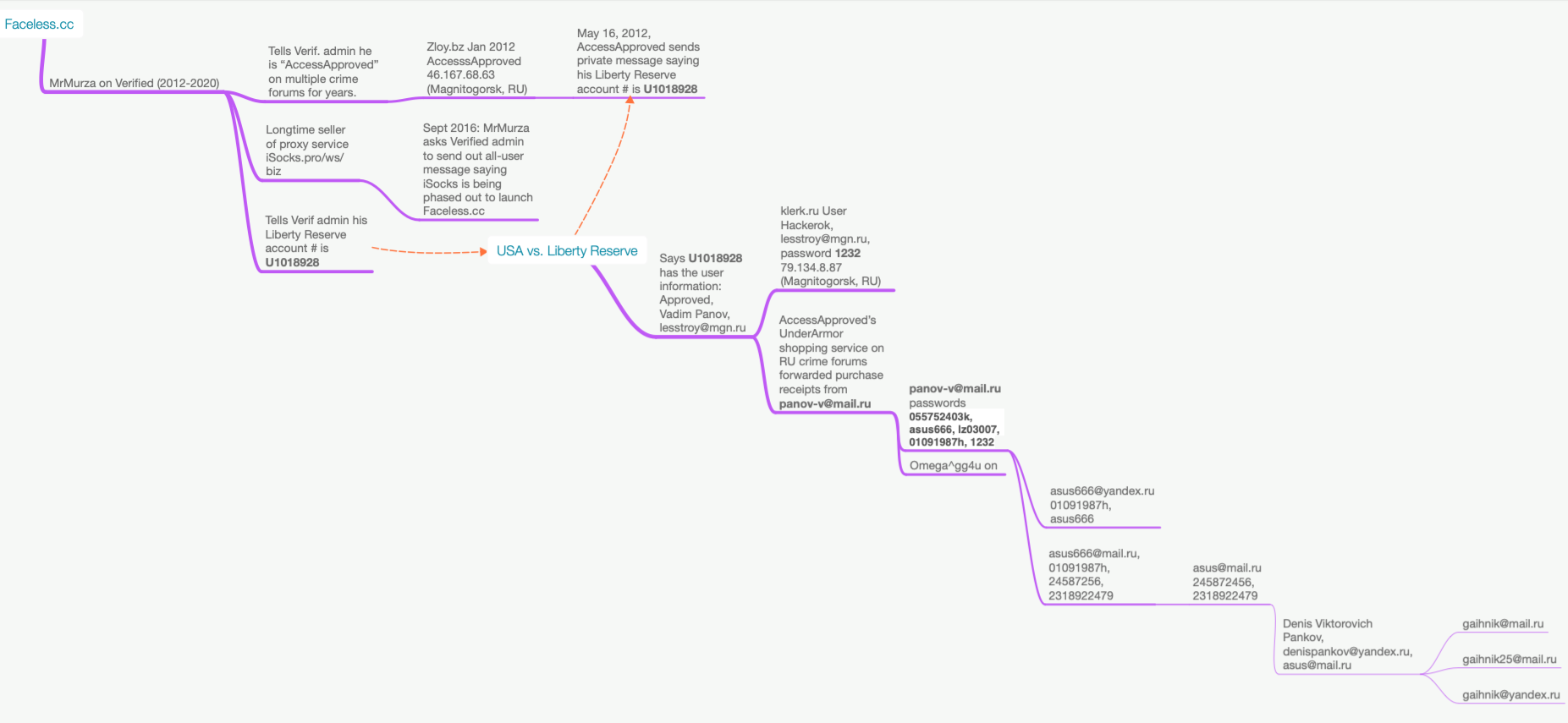
For less than a dollar per day, Faceless customers can route their malicious web traffic through tens of thousands of compromised systems advertised on the proxy service.
Names, bank account numbers, property transaction amounts, as well as identity card numbers were extracted from outdated database servers of the real estate firm by a cybercrime group in 2021.