Researchers revealed that the Vice Society ransomware group is utilizing a specialized tool based on PowerShell to escape detection and automate the data extraction process. With the adoption of increasingly sophisticated tools, Vice Society has become a formidable threat to organizations globally.
Hundred Finance confirmed the exploit on April 15, noting that it had contacted the hacker for negotiations. The platform is also working with security teams to resolve the issue and has urged anyone with information on the incident to reach out.
The flow of venture capital funding to cybersecurity firms hit a steep decline in the first quarter of 2023 compared with year-ago figures, lending more credence to the notion the industry may be oversaturated with vendors and overlapping tools.
The company said a hacker gained access to forum user data after compromising an administrator’s account. The attacker may have accessed information such as username, reputation, join date, post count, email addresses, and the last used IP address.
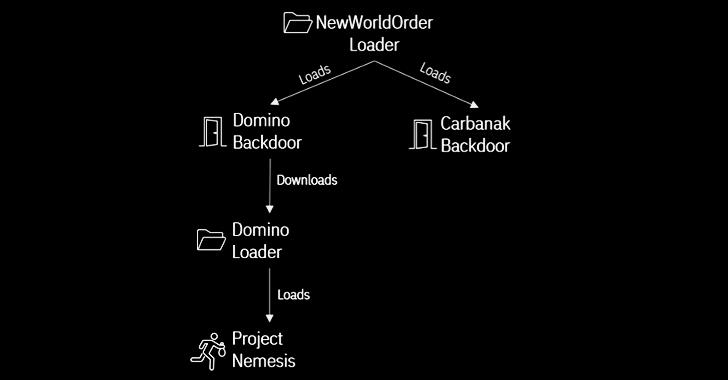
The latest intrusion wave, spotted by IBM Security X-Force two months ago, involves the use of Dave Loader, a crypter previously attributed to the Conti group (aka Gold Blackburn, ITG23, or Wizard Spider), to deploy the Domino backdoor.
Discovered by security researchers at Kaspersky, the malicious campaign relied on messages written in different languages, including English, German, Italian, and French.
A Chinese hacker group, Vixen Panda, is suspected of targeting the Foreign Ministry in a recent cyberattack. As per a new report by Euractiv, the hackers showed a keen interest in policy documents.
Over the weekend, Rheinmetall, a leading German armaments and technology company, was the victim of a cyberattack that targeted all three of its divisions. However, company officials have stated that the attack did not impact operations.
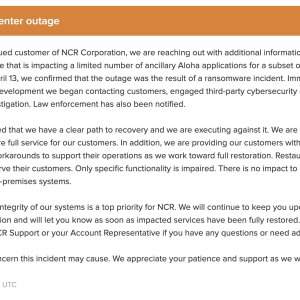
NCR is suffering an outage on its Aloha point of sale (PoS) platform since Wednesday after it was hit by a ransomware attack conducted by the BlackCat/ALPHV ransomware group.
They used a technique dubbed Business Email Compromise (BEC). As part of this, it’s claimed, the fraudsters broke into people’s email accounts, too, and chatted via mobile apps to organize their crimes.