The sensitive nature of legal data makes law firms lucrative targets for hackers, who aim to access valuable information for specific purposes. Despite the costly demands, firms face the dilemma of paying the ransom or risking backlash from clients.
According to Picus Security, organizations are failing to detect 44% of cyberattacks, revealing major exposure gaps. 40% of environments tested allowed for attack paths leading to domain admin access.
WeRedEvils announced their intention to target Iranian systems on Telegram, claiming their attack was successful in infiltrating Iran’s computer systems, stealing data, and causing the outage.
The lawsuit alleges that TikTok collected personal information from children under 13 without parental consent, failed to delete children-created accounts, and misled parents about data collection.
Unlike other ransomware groups targeting businesses, Magniber focuses on individuals. Victims report their devices getting infected after running software cracks. Ransom demands start at $1,000 and escalate to $5,000 if not paid within three days.
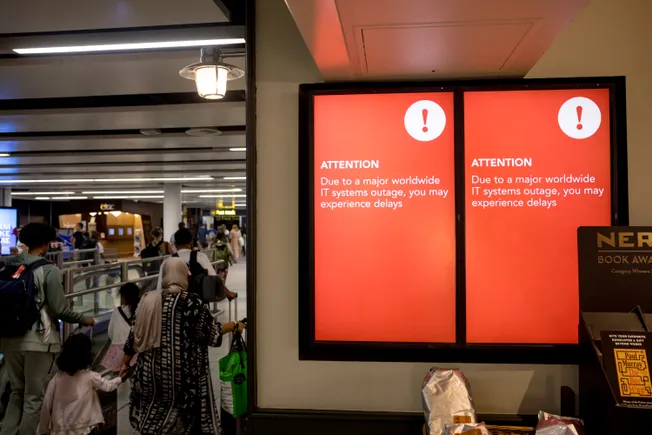
Federal officials have raised concerns about the software supply chain and memory safety vulnerabilities following a global IT outage caused by a faulty CrowdStrike software update.
Germany has summoned the Chinese ambassador over a cyberattack by a Beijing-backed threat actor on a cartography agency. The attack, aimed at espionage, was carried out at the end of 2021.
The Streamlining Federal Cybersecurity Regulations Act, led by senators Gary Peters and James Lankford, would create an interagency group to synchronize U.S. cyber regulatory regimes and establish a pilot program for testing new frameworks.
Hackers are targeting misconfigured Jupyter Notebooks using a repurposed Minecraft DDoS tool known as mineping. The attack, dubbed Panamorfi, involves utilizing a Java tool to launch a TCP flood DDoS attack against vulnerable Jupyter Notebooks.
This type of attack, known as Bytecode Jiu-Jitsu, takes advantage of the fact that interpreters do not require execution privilege for bytecode, making it difficult for security tools to detect.