LockBit’s similarities to BlackMatter come from overlaps in the privilege escalation and harvesting routines used to identify APIs for process termination as well as the use of anti-debugging and threading techniques designed to thwart analysis.
According to a post-mortem report published by Audius on Sunday, the hacker exploited a bug in the contract initialization code that allowed them to perform repeated invocations of the initialize functions.
The Minister for Foreign Affairs of Belgium claimed that several China-linked APT groups—APT27, APT30, and APT3—targeted the nation’s defense and interior ministries. However, the spokesperson of the Chinese Embassy in Belgium denied the accusations.
Checkmarx warned against a new supply-chain attack that involves spoofing metadata commits to deceive GitHub developers into using malicious code. Commits are essential components in the GitHub system and have a unique hash or ID. Fake commits can be automatically generated and added to the user’s GitHub activity graph, pretending as if they have been […]
Security researcher ProxyLife recently discovered that Qakbot has been abusing the Windows 7 Calculator app for DLL side-loading attacks since at least July 11. The method continues to be used in malspam campaigns.
In a Securities and Exchange Commission filing on Friday, the mobile phone company said the funds would pay for claims by class members, the legal fees of plaintiffs’ counsel, and the costs of administering the settlement.
Claroty researchers discovered that the FileWave MDM product is affected by two critical security holes: an authentication bypass issue (CVE-2022-34907) and a hardcoded cryptographic key (CVE-2022-34906). The vendor quickly patched the flaws.
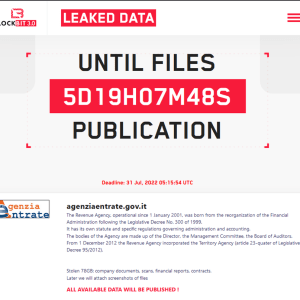
The ransomware gang LockBit claims to have hacked the Italian Revenue Agency (Agenzia delle Entrate) and added the government agency to the list of victims reported on its dark web leak site.
The scale of business email compromise (BEC) attacks is clear: according to the FBI, the combined total lost to BEC attacks is $43 billion and counting, with attacks reported in at least 177 countries.
Depending on what data was stolen, this attack could impact a large number of critical, and sensitive, organizations that use Entrust for identity management and authentication.