Written in .NET language and obfuscated with SmartAssembly, the loader makes use of compression and encryption to evade detection by antivirus software. It first appeared in March 2021 and has since been put for sale at a price of $59.
In a data breach notification issued on June 14, Comstar said it “immediately took steps to secure our network, and launched a thorough investigation, with the assistance of third-party experts, to determine the nature and scope of the incident”.
The latest example of this approach came in April, when U.S. authorities wiped malware off of hacked servers used to control a Russian intelligence agency’s botnet, preventing operators from sending instructions to the thousands of infected devices.
Internet infrastructure firm Cloudflare said today that it mitigated a 26 million request per second distributed denial-of-service (DDoS) attack, the largest HTTPS DDoS attack detected to date.
Conti claimed responsibility for the first attack against Costa Rica’s government and is believed to have some links to the ransomware-as-a-service operation HIVE, which was responsible for the second attack impacting the country’s healthcare system.
A new high-severity vulnerability has been disclosed in the Zimbra email suite that, if successfully exploited, enables an unauthenticated attacker to steal cleartext passwords of users sans any user interaction.
Tal Goldstein, head of strategy, Centre for Cybersecurity at the World Economic Forum Centre for Cybersecurity, explained that his organization has long been working at the global level to try and address the most pressing issues facing the world.
On June 12, 2017, ESET researchers published their findings about a malware that was capable of causing a widespread blackout. Industroyer, as they named it, was the first known piece of malware that was developed specifically to target a power grid.
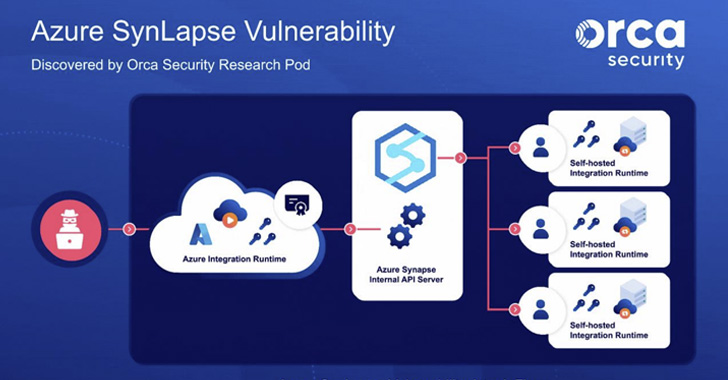
Microsoft has incorporated additional improvements to address the recently disclosed SynLapse security vulnerability in order to meet comprehensive tenant isolation requirements in Azure Data Factory and Azure Synapse Pipelines.
Researchers devised a new hardware attack aimed at Pointer Authentication in Apple M1 chip-based CPUs, that may allow an attacker to run arbitrary code on Mac systems. The attack is an exploitation technique but it cannot affect the system on its own. Apple has claimed that the issue does not pose an immediate risk to users […]