Phishing scams involving the delivery of parcels have resulted in a loss of at least S$574,000 (~$413,000) since the start of 2022. The scams have claimed at least 415 victims, the Singapore Police Force said.
The researcher found that when a Tesla is unlocked using the key card via NFC, there is a 130-second window when an attacker within Bluetooth range of the targeted vehicle can add their own key, which they can later use to unlock and drive the car.
CERT-UA says that Russian hackers launched a new malicious email campaign leveraging Follina and targeted more than 500 recipients at various media organizations in Ukraine, including radio stations and newspapers.
Three PyPI packages were found to contain a backdoor due to a malicious dependency within certain versions, thereby exposing users to supply chain attacks. The threat included with the ‘Keep’ package is pretty high as it particularly receives over 8,000 downloads per week on average. Even if PyPI did remove the request package, there are chances […]
Syslogk can force-load its modules into the Linux kernel (versions 3.x are supported), hide directories and network traffic, and eventually load a backdoor called ‘Rekoobe.’
A Chinese APT known as Gallium has been observed using a previously undocumented remote access trojan in its espionage attacks targeting companies operating in Southeast Asia, Europe, and Africa.
In a panel session at the RSA Conference 2022, a panel of experts discussed the implications and the opportunities for the US Department of Defense’s Cybersecurity Maturity Model Certification (CMMC) Program.
The bad practices highlighted by CISA include the use of unsupported or end-of-life software, the use of known/fixed/default credentials, and the use of single-factor authentication for remote or administrative access.
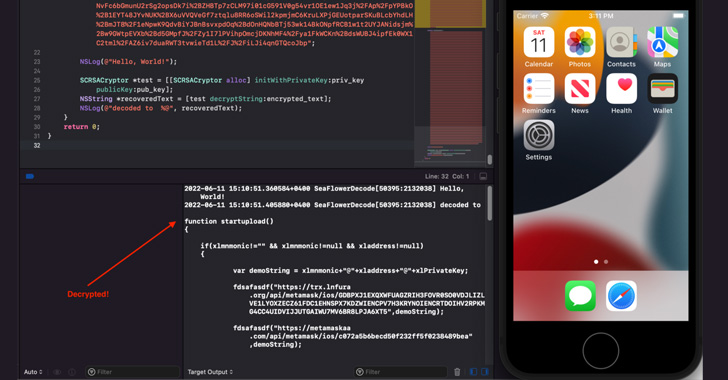
A threat actor known as SeaFlower has been targeting Android and iOS users as part of an extensive campaign that mimics official cryptocurrency wallet websites intending to distribute backdoored apps that drain victims’ funds.
A series of two batches of data the Aqua Security researchers accessed using the Travis CI programming interface yielded 4.28 million and 770 million logs from 2013 through May 2022.