Researchers have identified an increase in activity by a new hacktivist group called Cyber Spetsnaz that has been targeting NATO infrastructure. In April, Cyber Spetsnaz created its first division called Zarya, with a bunch of experienced penetration testers, OSINT specialists, and hackers. The group is strongly believed to be state-sponsored.
Recently, Onapsis researchers detected exploitation activity related to three vulnerabilities that were already patched by SAP – CVE-2021-38163, CVE-2016-2386, and CVE-2016-2388.
Current phishing emails run the gamut from airline ticket giveaways, gift cards, and offers of bonus flight hours to booking confirmations and bargain offers for holiday rentals and all-inclusive deals.
Recent analysis of ransomware attack trends by Akamai highlights the risks and suggest mitigation, while an analysis of Web app and API attack trends offers a fresh look at the infection vectors used by ransomware operators and others.
Both the tools used and the threat posed by common cybercriminals pale in comparison to the tools used by more professional groups such as the famous hacking groups and state-sponsored groups.
With the 2022 election season around the corner, campaigns of all sizes need to be prepared for a widened set of potential cybersecurity risks, experts and a top intelligence official said.
The team of IT security researchers at vpnMentor led by Noam Rotem identified a misconfigured Microsoft Azure server that exposed the personal and educational records of tens of thousands of students from India and Israel.
The threat actor has a history of using document lures with pornographic themes to infect users and makes heavy use of USB shortcut techniques to spread the malware and infect additional targets.
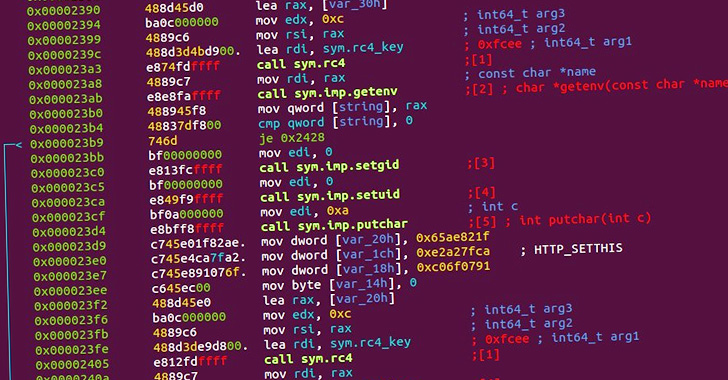
Cybersecurity researchers have taken the wraps off what they call a new “nearly-impossible-to-detect” Linux malware that could be weaponized to backdoor infected systems.
Attackers are exploiting vulnerabilities affecting Cisco devices, four affecting QNAP devices, two affecting Pulse Secure devices, and one each in devices from Citrix, D-Link, Fortinet, Netgear, MikroTik, and DrayTek.