Critical infrastructure providers are urging federal officials for more flexibility in reporting cyber incidents within the first 72 hours under the Cyber Incident Reporting for Critical Infrastructure Act.
Attackers can leverage the Jenkins Script Console to execute malicious Groovy scripts, leading to cybercriminal activities such as the deployment of cryptocurrency miners.
The shift away from public disclosure on Twitter is part of an evolution in how the CNMF communicates cyber threat information. The command now focuses on working closely with industry partners to share information effectively and efficiently.
The flaw allows an attacker to execute arbitrary commands as root on the affected device’s operating system. Only attackers with administrator credentials can successfully exploit this vulnerability.
The emails falsely accuse recipients of sexual offences, using names and seals of authorities to appear authentic. Citizens are advised not to respond to such emails and report them to authorities.
Avast researchers have identified a cryptographic weakness in the DoNex ransomware and its previous versions, enabling them to create a decryptor for files encrypted by these variants.
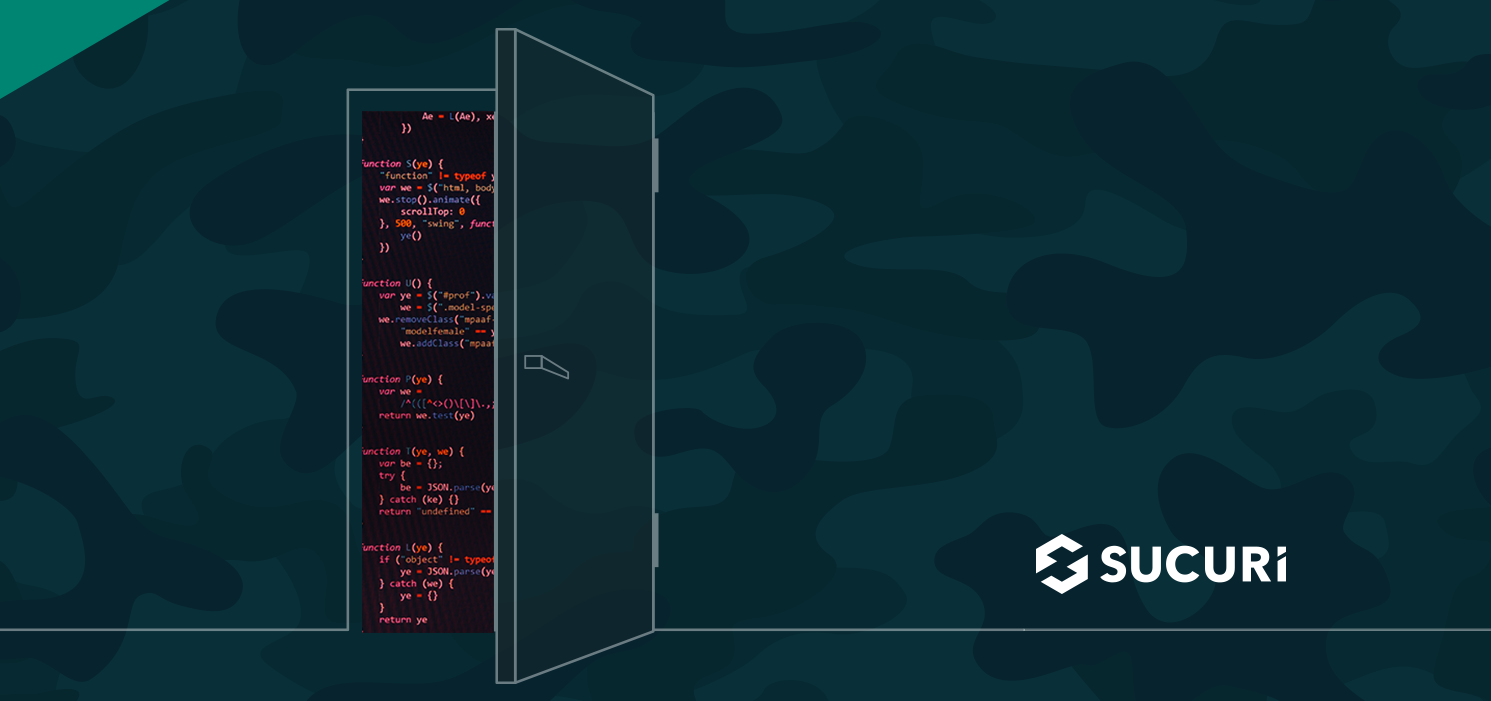
A new variation of WordFence evasion malware has been discovered, concealing backdoors in infected WordPress environments. A suspicious plugin named “wp-engine-fast-action” was found tampering with the popular WordFence security plugin.
The EU Commission is offering over €210m ($227.3m) in funding for cybersecurity and digital skills programs through the Digital Europe Programme (DEP). About $38m will go towards projects protecting critical infrastructures.
Team ARXU gained recognition earlier this year for targeting Romania over its support for Israel. The hacker group has a history of cyberattacks against Israel and its allies.
Information-stealing malware families have evolved to impersonate generative AI tools, with examples like GoldPickaxe stealing facial recognition data for deepfake videos.