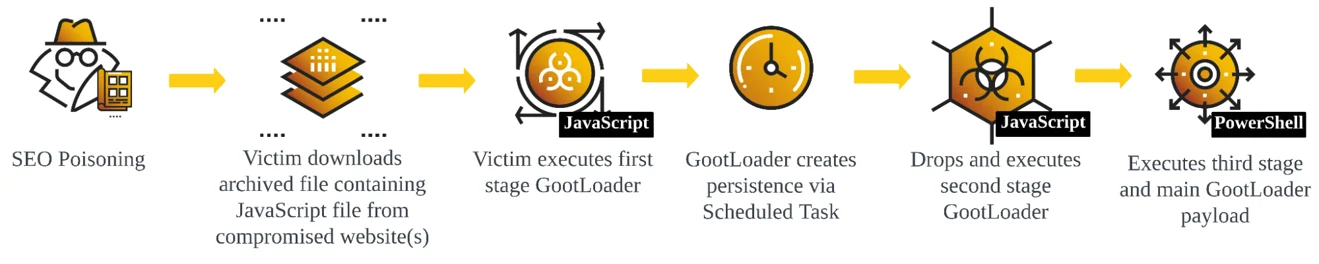
The malware has evolved into multiple versions, with GootLoader 3 being the latest one in use. Despite updates to the payload, the infection strategies have remained consistent since its resurgence in 2020.
The vulnerability could be exploited to compromise systems without requiring user interaction, contrary to some severity assessments initially made by Tenable and Red Hat.
Eldorado also encrypts network shares using the SMB protocol, deletes shadow volume copies, and skips certain file types to prevent system damage. Affiliates can customize attacks on Windows, while Linux customization is limited.
Traeger grills face security bugs that could spell trouble for BBQ enthusiasts. High-severity vulnerabilities in the Traeger Grill D2 Wi-Fi Controller could allow remote attackers to control the grill’s temperature or shut it down.
Online accounts are increasingly protected by passkey technology, but many platforms like banking, e-commerce, social media, and software development can still be compromised using adversary-in-the-middle (AitM) attacks.
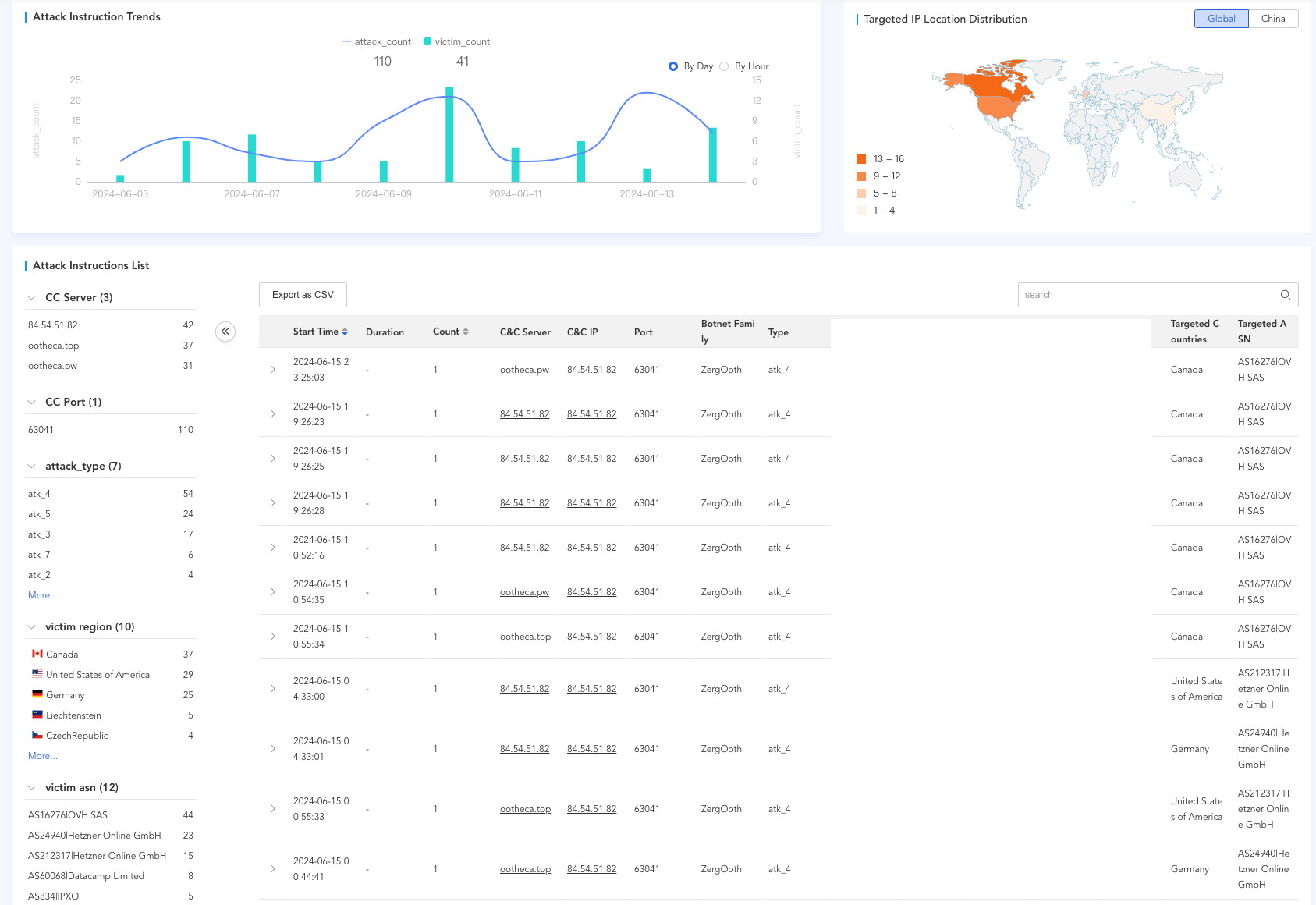
The researchers at QiAnXin XLab team discovered a new Golang-based botnet called Zergeca, capable of conducting DDoS attacks. It was detected through a suspicious ELF file and has been used to launch DDoS attacks in Canada, the U.S., and Germany.
The Turla malware has been found using weaponized LNK files to infect computers. The malware leverages a compromised website to distribute malicious packages through phishing emails.
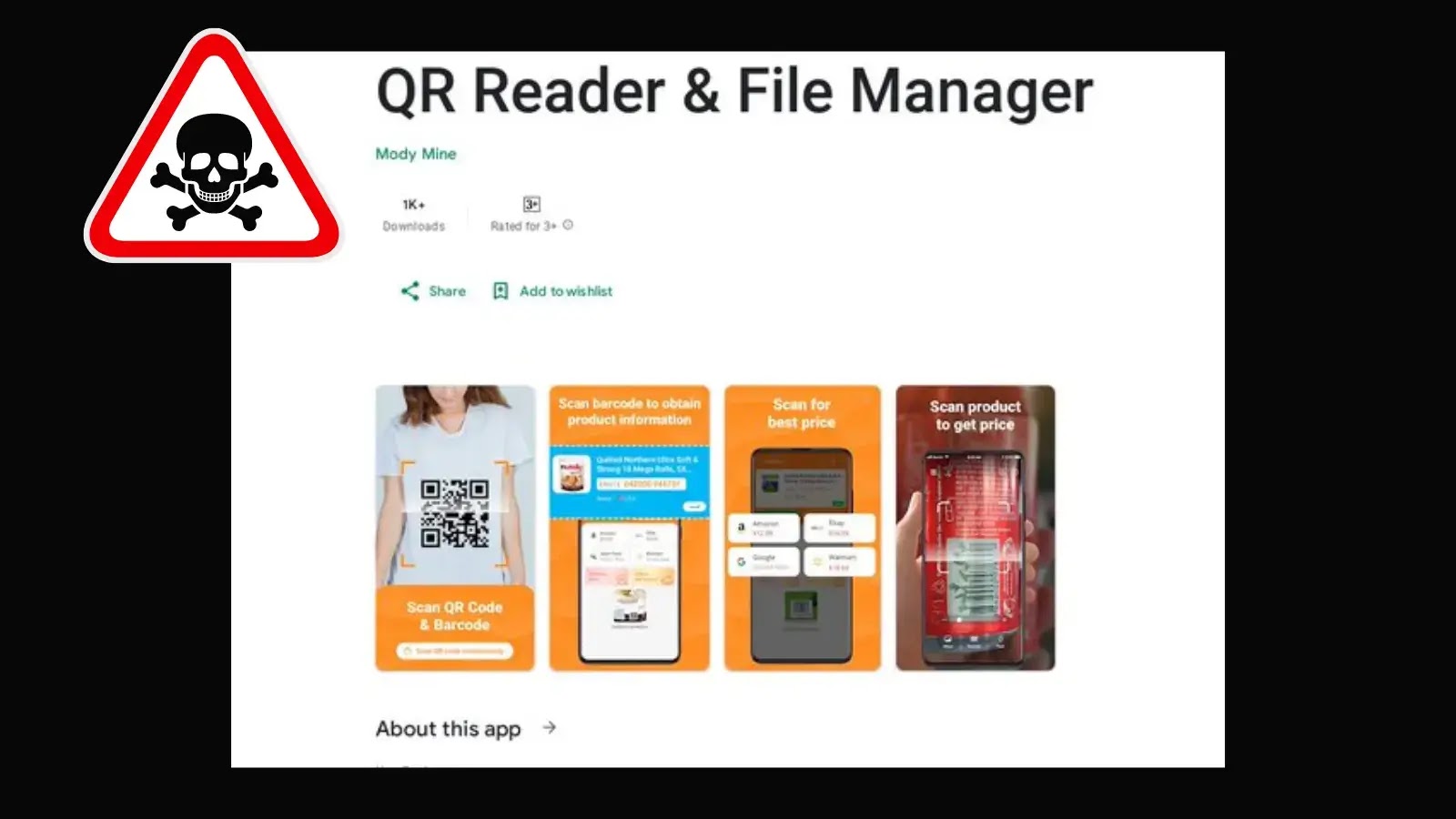
A malicious QR code reader app on Google Play has been found distributing the Anatsa banking malware, posing a significant threat to users’ financial data. The app has already been downloaded thousands of times.
ANSSI warned about a hacking group linked to Russia’s SVR targeting French diplomatic interests. The group has compromised email accounts at the French Ministry of Culture and the National Agency for Territorial Cohesion
Hackers are targeting older versions of the HTTP File Server from Rejetto to drop malware and cryptocurrency mining software by exploiting a critical vulnerability (CVE-2024-23692) that allows executing arbitrary commands without authentication.