According to the Australian Competition & Consumer Commission, the losses reported in Q1 2022 are estimated to be $270,000 (up by 301% compared to 2021), which add up to losses incurred by victims who previously fell for the same type of scam.
Tufin announced that it has entered into a definitive agreement to be acquired by Turn/River Capital, a software-focused investment firm, in an all-cash transaction that values the company at about $570 million.
Upon discovering the intrusion, Parker shut down some systems and launched an investigation. Law enforcement has been notified and cybersecurity and legal experts have been called in to assist.
WhiteSource launched WhiteSource Spring4Shell Detect, a free command-line interface (CLI) tool that quickly scans projects to find vulnerable open source libraries for CVE-2022-22965, also known as Spring4Shell.
e-Commerce sites are frequently targeted by cyberattackers and there isn’t much attention paid to the cybersecurity measures at brick-and-mortar retailers. Many cybercriminal groups rely on banking trojans to steal customer credit/debit card information or internet banking credentials from the networks of retailers. Online retailers are suggested to review their budgets and allocate an adequate portion to […]
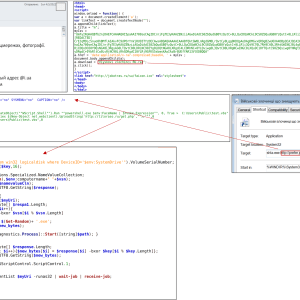
CERT-UA published a security advisory to warn of spear-phishing attacks conducted by Russia-linked Armageddon APT (aka Gamaredon, Primitive Bear, Armageddon, Winterflounder, or Iron Tilden) targeting local state organizations.
Washington, DC-based API security firm Corsha has raised $12 million in a Series A funding round led by Ten Eleven Ventures and Razor’s Edge Ventures, with participation from 1843 Capital.
Colibri Loader is a relatively new piece of malware that first appeared on underground forums in August 2021 and was advertised to “people who have large volumes of traffic and lack of time to work out the material“.
CVE-2021-45382 is a Remote Code Execution (RCE) vulnerability that exists in all series H/W revisions D-Link DIR-810L, DIR-820L/LW, DIR-826L, DIR-830L, and DIR-836L routers via the DDNS function in ncc2 binary file.
Hive ransomware gang is using a new IPfuscation tactic to hide its payload wherein they hide 64-bit Windows executables in the form of an array of ASCII IPv4 addresses. Additionally, the researchers spotted additional IPfuscation variants using IPv6 instead of IPv4 addresses, UUIDs, and MAC addresses, all operating in almost the same way.