Fraud and computer misuse offenses rose by 43% in the year ending June 2021 compared with the pre-COVID year ending June 2019, according to estimates from the Telephone-operated Crime Survey for England and Wales (TCSEW).
Ukraine’s security service, the SBU, has revealed the identities of five individuals allegedly involved in cyberattacks attributed to a Russia-linked threat group named Gamaredon.
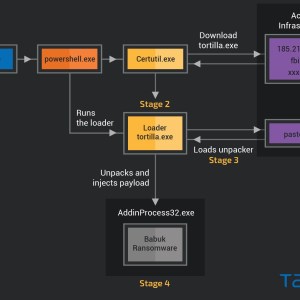
Talos researchers warn of a new threat actor that is hacking Microsoft Exchange servers by exploiting ProxyShell flaws to gain access to corporate and deploy the Babuk Ransomware.
The Federal Bureau of Investigation (FBI) warns that victims of various fraud schemes are increasingly asked by criminals to use cryptocurrency ATMs and Quick Response (QR) codes, making it harder to recover their financial losses.
Researchers have released public exploit code and a proof of concept tool to test Bluetooth devices against System-on-a-Chip (SoC) security bugs impacting multiple vendors, including Intel, Qualcomm, Texas Instruments, and Cypress.
The US State Department announced a $10 million reward for any information leading to the identification or location of any individuals holding key leadership positions in the DarkSide ransomware variant transnational organized crime group.
The ‘coa’ library, short for Command-Option-Argument, receives about 9 million weekly downloads on npm, and is used by almost 5 million open source repositories on GitHub.
BlackMatter ransomware group included a new data exfiltration tool called Exmatter to hasten its information-stealing process from victims’ networks. The tool has been developed using the DotNet framework. Organizations are suggested to use robust anti-ransomware solutions to stay protected and stay informed on future updates to this threat.
Researchers have disclosed a security flaw in the Linux Kernel’s Transparent Inter Process Communication (TIPC) module that could potentially be leveraged both locally as well as remotely to execute arbitrary code within the kernel.
Over the past year and a half, the threat actor has compromised the networks of at least eight French companies, stealing data and deploying malware from multiple ransomware-as-a-service (RaaS) operations.