The Grandoreiro banking Trojan has resurfaced with major updates, including enhanced functionality and the ability to target over 1500 global banking applications and websites in more than 60 countries, making it a more potent threat.
Experts highlight the need for better collaboration within the cybersecurity vendor ecosystem to help security teams defend against increasing automated, machine-generated cyberattacks.
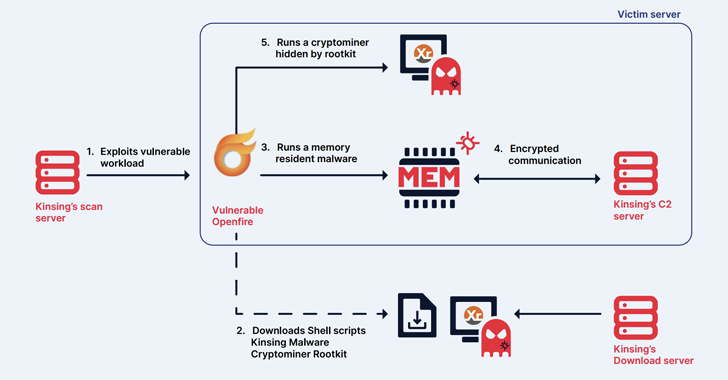
The Kinsing hacker group has demonstrated its ability to continuously evolve and adapt, quickly integrating newly disclosed vulnerabilities into its exploit arsenal to expand its cryptojacking botnet across various operating systems and platforms.
Gomir shares many similarities with GoBear and features direct command and control (C2) communication, persistence mechanisms, and support for executing a wide range of commands.
Deuterbear, while similar to Waterbear in many ways, shows advancements in capabilities such as including support for shellcode plugins, avoiding handshakes for RAT operation, and using HTTPS for C&C communication.
The May 2024 campaign, dubbed UNK_SweetSpecter, employs the SugarGh0st RAT, a remote access trojan tailored from the Gh0stRAT. This variant, historically linked to Chinese-speaking threat actors, has now been repurposed to target AI-related entities.
Researchers with the Slovak cybersecurity firm ESET published a technical analysis on Wednesday of the two backdoors by a suspected Russian threat group, which they named LunarWeb and LunarMail.
A new Android banking Trojan called “Antidot” is targeting users across multiple regions by mimicking a Google Play update app and incorporating various malicious features like overlay attacks, keylogging, and remote control capabilities.
The challenges within the AI supply chain mirror those of the broader software supply chain, with added complexity when integrating large language models (LLMs) or machine learning (ML) models into organizational frameworks.
The SEC now requires certain financial institutions to have written policies for detecting, addressing, and notifying customers of data breaches involving their personal information.