Google singled out nine apps—with over 5.8 million combined downloads—masqueraded as genuine apps such as Horoscope Daily and Rubbish Cleaner to steal Facebook login details. Before and after installing any app, users must stay vigilant for unusual activity and permissions required by the apps.
Netskope was valued at $7.5 billion after it raised $300 million in a funding round led by existing investor ICONIQ Growth, with participation from other existing investors.
The CSA said attackers capitalised on pandemic-related anxiety, targeting e-commerce, data security, vaccine-related research, and operations, including contact-tracing operations.
Cybercriminals seek illicit marketplaces with a reputation for serving their needs while being operationally secure and trustworthy, much like business deals are conducted in traditional economies.
Magecart hackers have latched on to a new technique of obfuscating the malware code within comment blocks and encoding stolen credit card data into images and other files hosted on the server.
Before claiming responsibility for a breach at the software company Kaseya, the group accounted for less than 10% of known ransomware victims, according to the threat intelligence firm Recorded Future. Now, it accounts for 42%.
Netskope’s valuation more than doubled to $7.5 billion after a $300 million funding round led by ICONIQ Growth, highlighting massive demand for cloud security services as cyber-attacks increase in number and severity.
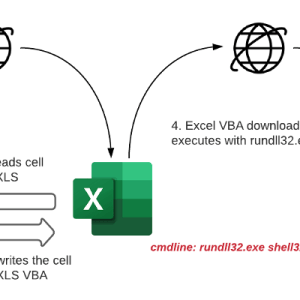
Hackers use a new technique in malspam attacks to disable Macro security warnings in weaponized docs
Experts from McAfee Labs warn of a novel technique used by threat actors that are using non-malicious documents to disable security warnings prior to executing macro code on the recipient’s PC.
15 Philips Vue Vulnerabilities located in the Philips Clinical Collaboration Platform Portal represent dangerous tools in the hands of a hacker as they could cause remote code execution cyberattacks.
Comparis said its website – which lets consumers compare prices for goods and services – was working normally again, but access via e-mail and customer hotline may still be limited as it works with cybersecurity specialists on a complete recovery.