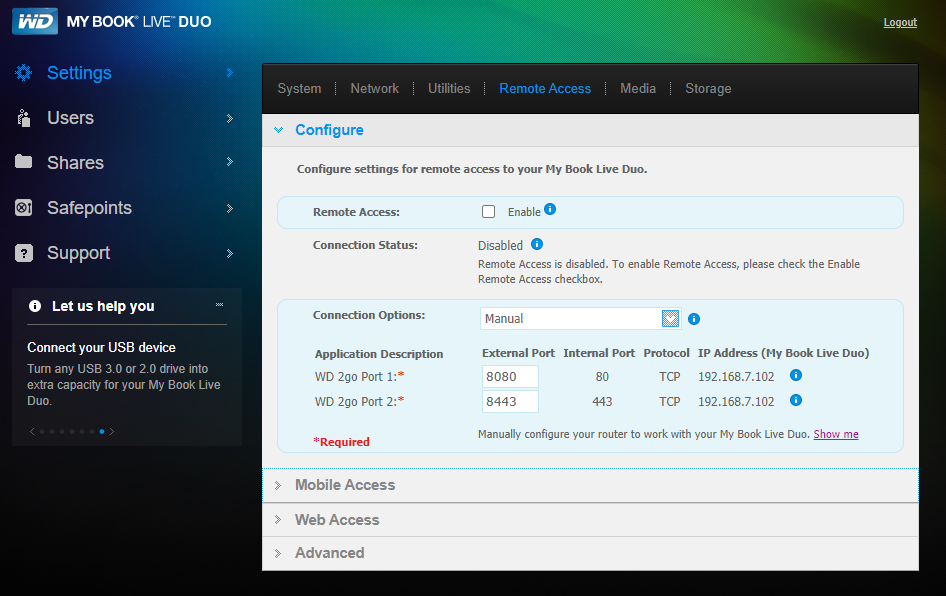
Western Digital is urging users of its MyBook Live brand of network storage drives to disconnect them from the Internet, warning that malicious hackers are remotely wiping the drives using a critical flaw.
Seemingly, a variant of the ransomware, Epsilon Red, relies on vulnerable Microsoft Exchange servers. Threat actors use them to launch mass server exploitation campaigns and try to expose companies’ information for revenue.
The researchers at Trustwave have disclosed in a recent report that threat actors are starting to utilize WIM (Windows Imaging Format) attachments in order to distribute the Agent Tesla remote access trojan.
Researchers have discovered a strain of cryptocurrency-mining malware that abuses Windows Safe mode during attacks. The malware, dubbed Crackonosh by researchers at Avast, spreads through pirated and cracked software.
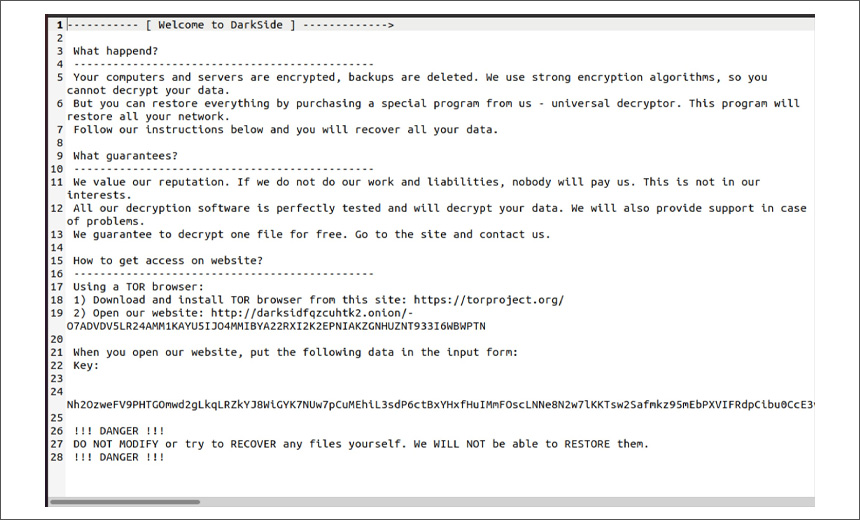
The DarkSide Russian-speaking cybercrime group, which announced it was closing its ransomware-as-a-service operation, had earlier completed a Linux version of its malware designed to target ESXi servers hosting VMware virtual machines.
Microsoft said on Friday an attacker had won access to one of its customer-service agents and then used information from that to launch hacking attempts against customers.
Researchers developed an attack technique named Adversarial Octopus that could perform a targeted attack on AI-based facial recognition systems. This attack shows that AI systems require much more attention at the security front, and such new attack methods will help raise awareness.
Cl0p ransomware hackers just dumped stolen data on their dark website claiming it was stolen from a new victim. Several gang members of the group were detained by Ukrainian police last week but it seems the group is still active. Organizations are advised to proactively follow adequate security measures to stay protected.
After a months-long absence, the malware loader JSSLoader returned in June 2021 cyberattack campaigns by TA543 threat actor, rewritten from the .NET programming language to C++.
The database contained admin and user information, including WordPress login URLs, names, email addresses, usernames, roles, host IP addresses, timestamps, and configuration and security information.