Of all the critical infrastructure, water might be the most vulnerable to hacks: the hardest in which to guarantee basic cybersecurity hygiene, and the easiest in which to cause real-world harm.
Cybersecurity firm Quick Heal Technologies Ltd on Thursday said that it has detected a new batch of 8 Joker malware-laced apps with a cumulative download count of 50,000 on Google Play Store.
Law enforcement officials are making notable gains, including the FBI’s Colonial Pipeline action and the Netwalker takedown in January, both of which involved cryptocurrency seizures
Researchers at the Zhejiang University and the University of Michigan found a way to blind autonomous vehicles to obstacles using simple audio signals to tamper with the camera sensor.
SLSA – short for Supply chain Levels for Software Artifacts – aspires to provide security guidance and programmatic assurance to help defend the software build and deployment process.
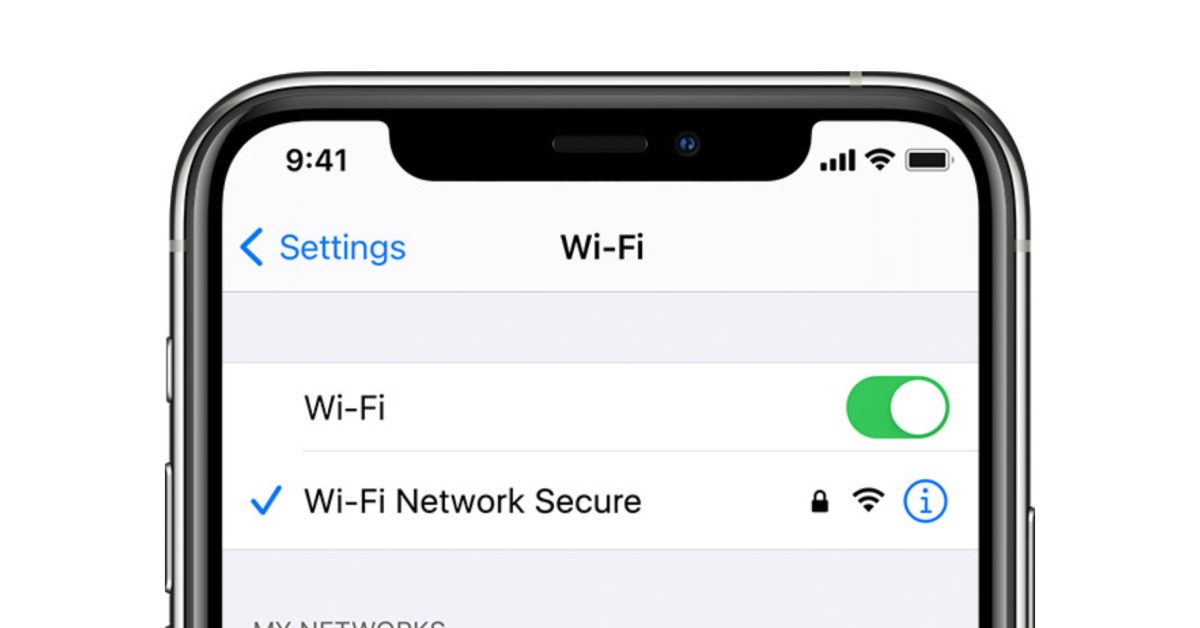
A security researcher has found that a carefully crafted network name causes a bug in the networking stack of iOS and can completely disable your iPhone’s ability to connect to Wi-Fi.
The Conti ransomware group has spent more than a year attacking organizations where IT outages can have life-threatening consequences such as hospitals, 911 dispatch carriers, emergency medical services, and law enforcement agencies.
Top Polish government officials have been hit by a far-reaching cyber attack conducted from Russian territory, Poland’s de facto leader Jaroslaw Kaczynski said on Friday in his first official statement on an email hacking incident this month.
Sophos researchers uncovered a malware campaign that aims at blocking infected users’ from visiting a large number of websites dedicated to software piracy by modifying the HOSTS file on the infected system.
The vulnerabilities impact devices running firmware versions prior 1.2.0.6 and which have the web-based management interface enabled. The expert pointed out that the interface is enabled by default.