Law enforcement authorities seized the Lockbit group’s Tor website again and they plan to reveal the identities of the LockBitSupps and other gang members on May 7, 2024.
The Israeli startup founded in 2022 by Or Eshed and David Weisbrot has raised $26 million in Series A funding. This round, led by Glilot+ and with participation from Dell Technologies Capital, brings LayerX’s total investment to $34 million.
The Cybersecurity and Infrastructure Security Agency sent out alerts to critical infrastructure sectors, with only 852 organizations responding by patching, implementing controls, or taking devices offline.
These hackers are employing sophisticated phishing techniques to distribute malicious software and target financial theft, with incidents steadily increasing over the past two years.
Path traversal vulnerabilities, also known as directory traversal, can be exploited by attackers to manipulate critical files, compromise security mechanisms, access sensitive data, and disrupt systems.
The Android bug discovered by a Mullvad VPN user reveals that Android devices can leak DNS queries even with the “Always-on VPN” feature and “Block connections without VPN” option enabled.
Nation-state threat actors like Sandworm used their own dedicated proxy botnets, while APT group Pawn Storm had access to a criminal proxy botnet of Ubiquiti EdgeRouters.
According to Gartner, 63% of organizations worldwide have fully or partially implemented a zero-trust strategy. For 78% of organizations implementing a zero-trust strategy, this investment represents less than 25% of the overall cybersecurity budget.
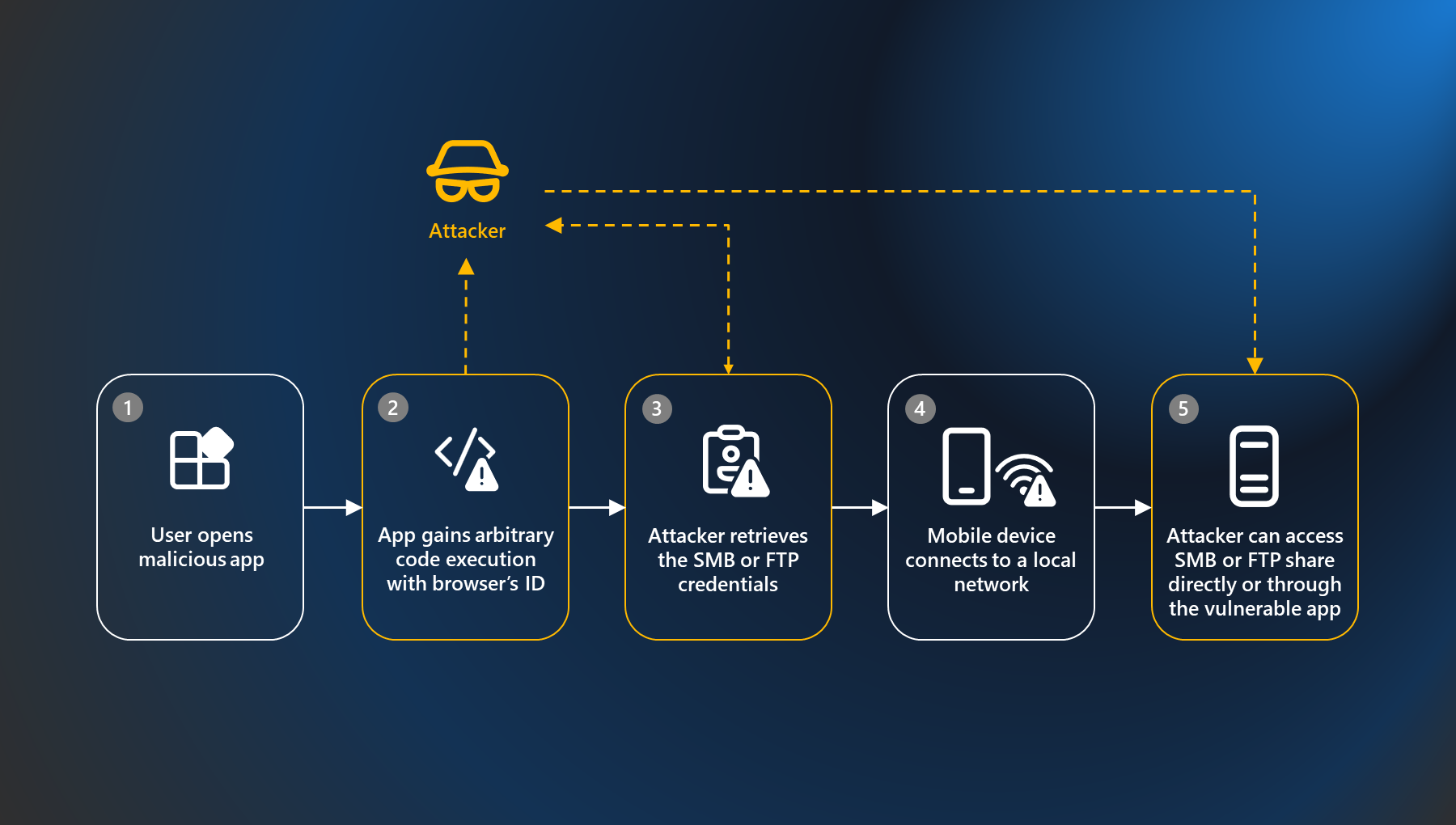
A vulnerability in popular Android apps like Xiaomi File Manager and WPS Office could allow malicious apps to overwrite files in the vulnerable app’s home directory, potentially leading to code execution and unauthorized access to user data.
Xiaomi resolved 20 flaws, ensuring user safety by fixing issues like arbitrary access to system components and data leaks. Google also fixed six vulnerabilities, including geolocation access through the camera and arbitrary file access.