The EPUB format relies primarily on XHTML and CSS to construct e-books, with browser engines often used to render their contents, which leads to browser-like vulnerabilities.
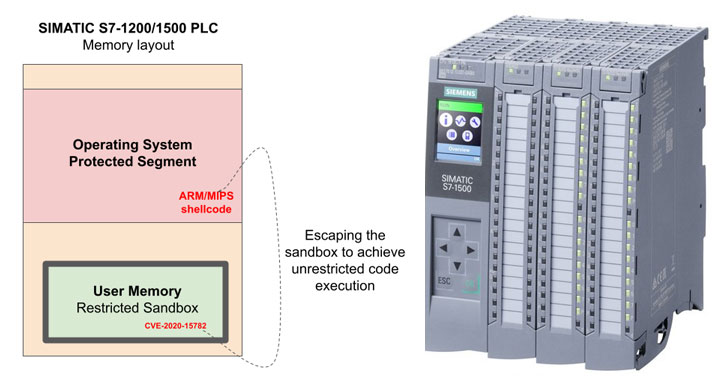
Siemens said an unauthenticated, remote attacker with network access to TCP port 102 could write arbitrary data and code to protected memory areas or read sensitive data to launch further attacks.
Law enforcement authorities in Mexico arrested the alleged head of a financial fraud operation that used infected ATMs to steal more than $1 billion from tourists in recent years.
President Joe Biden’s fiscal 2022 budget blueprint released Friday proposes $750m for the federal government to implement lessons learned from the SolarWinds hack that compromised nine agencies.
The leak was revealed by investigative journalism website Bellingcat, which described the findings after “simply searching online for terms publicly known to be associated with nuclear weapons.”
These emails do not explain what you are unsubscribing or subscribing to and are being used by spammers to verify if the recipient’s email is valid and susceptible to future phishing scams.
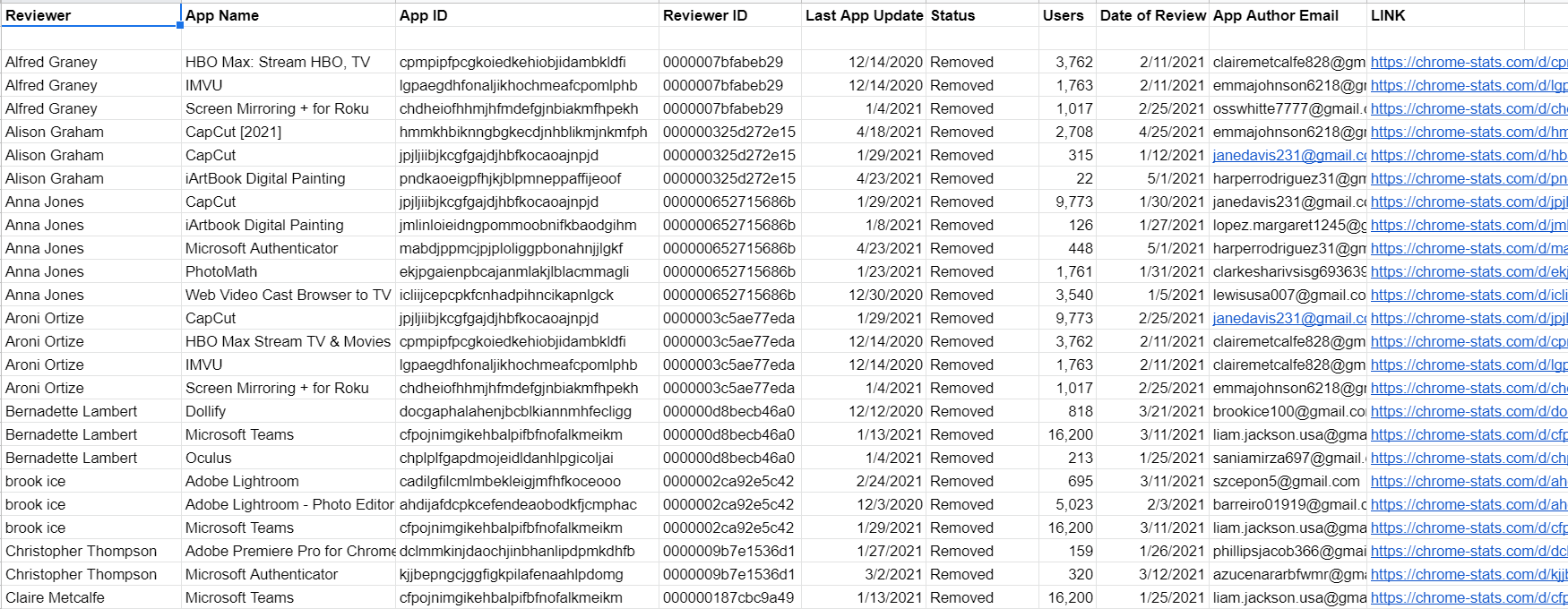
Leaving aside the extensions which are outright fraudulent, many legitimate extensions get abandoned or sold each year to shady marketers that it’s wise to only trust actively maintained extensions.
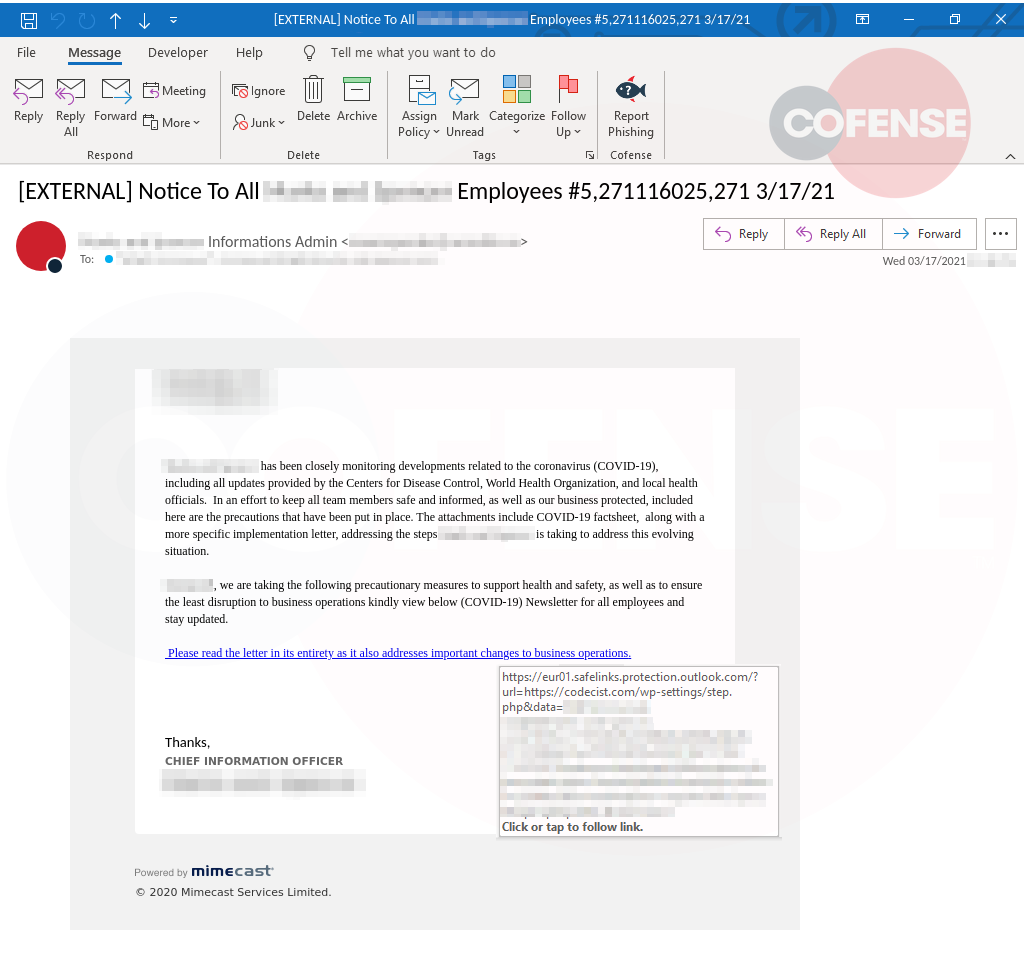
The Cofense Phishing Defense Center (PDC) has observed a phishing campaign that attempts to gather login credentials from employees by acting as the Chief Information Officer (CIO).
Deadshot monitors GitHub pull requests in real-time. The open-source tool flags the potential inclusion of sensitive data in any code, as well as “changes to sensitive functionality”.
Officials described the cyberattack as “basic phishing” in which hackers used malware-laden emails to target the systems of U.S. and foreign government agencies, think tanks, and humanitarian groups.