Security researchers have documented an attack technique that may allow attackers to leverage a legitimate Amazon VPC feature to mask their use of stolen API credentials inside AWS.
The notorious cybercrime gang behind the Carbanak RAT is spreading a backdoor called Lizar under the guise of a Windows pen-testing tool for ethical hackers. Experts say the group may be planning to further sharpen its tools and techniques to make its attacks stealthier and more effective.
APT36 was found creating fake domains to impersonate military and defense firms and disseminate malware-laced documents to infect victims with ObliqueRAT and CrimsonRAT. Organizations are recommended to stay vigilant and implement adequate security measures proactively.
A total of 12 design and implementation flaws in IEEE 802.11 technical standards leave all WiFi devices vulnerable to attacks. These flaws can be exploited by attackers within the radio range of the target.
Defenders need to be 100% perfect at protecting 100% of the countless entry points 100% of the time in order to prevent breaches, while on the other hand, hackers only need one exploit that works.
Several security researchers and security firms who reviewed last week’s security updates considered the bug the most dangerous vulnerability Microsoft fixed in this month’s patch cycle.
With an unprecedented number of people working remotely, phishing and ransomware attacks increased by 11 percent and 6 percent respectively, with instances of misrepresentation increasing by 15 times.
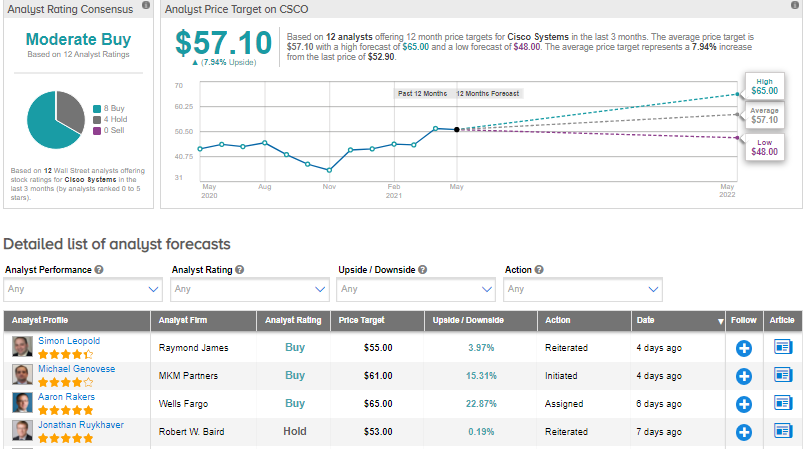
Cisco Systems (CSCO) plans to acquire privately-held California-based Kenna Security in a bid to enhance its security offerings. However, the financial terms of the deal were not disclosed.
Three hacking forums have now banned ransomware ads, three ransomware leak sites have gone down, and two other ransomware groups have announced plans to stop operating in public and go “private.”
BluBracket on Thursday said it raised $12 million in Series A funding so it can continue to work with DevSecOps teams to build security into products from the start and shift code development left.