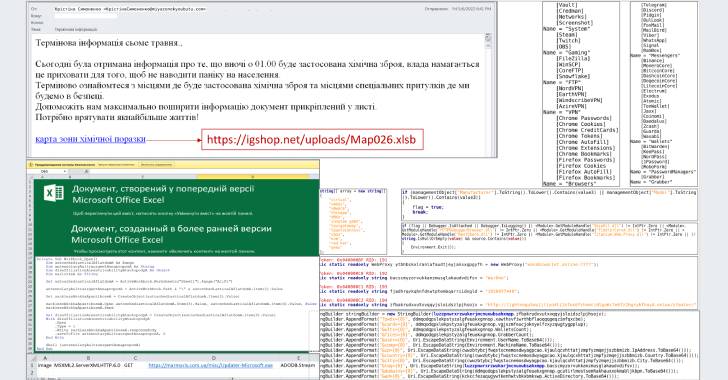
Ukrainian CERT Warns Citizens of a New Wave of Attacks Distributing Jester Malware
The attack, which requires potential victims to enable macros after opening the document, works by downloading and executing an .EXE file that is retrieved from compromised web resources, CERT-UA detailed.