Zscaler ThreatLabz has identified significant code similarities between Nevada and Nokoyawa ransomware including debug strings, command-line arguments, and encryption algorithms
A North Korean espionage group tracked as UNC2970 has been observed employing previously undocumented malware families as part of a spear-phishing campaign targeting U.S. and European media and technology organizations since June 2022.
About 92% of organizations have fallen victim to successful phishing attacks in the last 12 months, while 91% of organizations have admitted to experiencing email data loss, according to Egress.
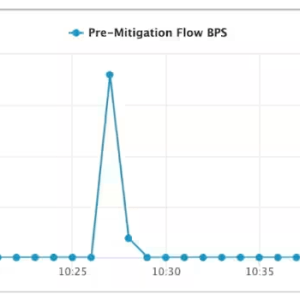
The company pointed out that the attack was intense and short-lived, with most attack traffic bursting during the peak minute of the attack. The overall attack lasted only a few minutes.
In 2022 there was a significant increase in API-related CVEs, growing +78% from H1 to H2. Although growth has stabilized over the past two quarters, the research team at Wallarm expects an increase in 2023.
Named “Xenomorph 3rd generation” by the Hadoken Security Group, the threat actor behind the operation, the updated version comes with new features that allow it to perform financial fraud in a seamless manner.
The UK-based digital identity company, led by CEO Robin Tombs, intends to use the funds to develop its technology that protects customers’ identities and personal data online.
In recent weeks, SentinelLabs observed novel Linux versions of IceFire ransomware being deployed within the enterprise network intrusions of several media and entertainment sector organizations worldwide.
“Customer Proprietary Network Information from some wireless accounts was exposed, such as the number of lines on an account or wireless rate plan,” AT&T told BleepingComputer.
An interior ministry spokesperson on Tuesday confirmed that the German government was carrying out a general review of telecoms tech suppliers, but said that this was not directed at specific manufacturers.